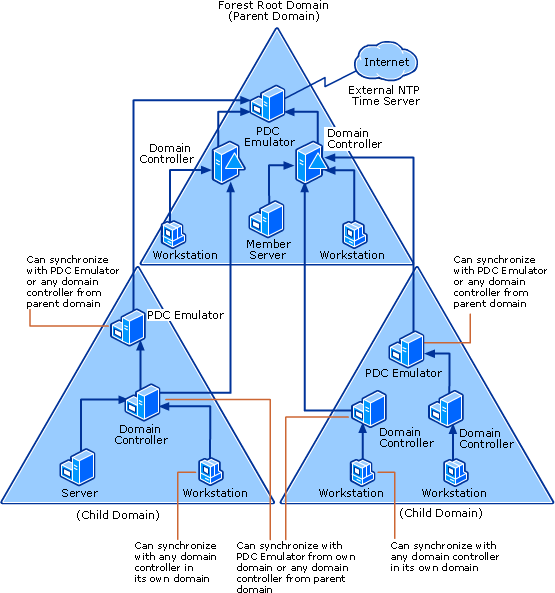
NTP in a Windows Domain
- In a Windows environment the forest root PDC emulator connects to a external reliable NTP source.
- PDC emulators in child domains synchronise their time with the PDC emulator or a DC in the parent domain.
- DCs in child domains can synchronise their time with the PDC emulator from their own domain or any DC from the parent domain.
- Workstations and member servers synchronise their time with any DC in their own domain.
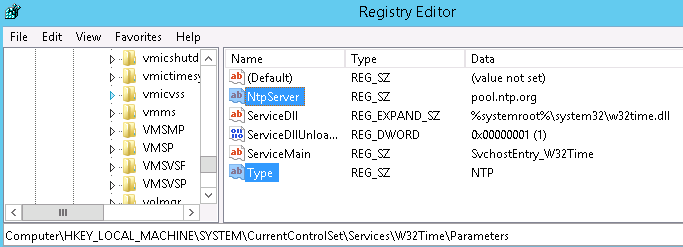
The NTP time process outlined above does not necessarily take place in a Windows environment. Check HKLM on a node (path below), in this example the client is a Type of NTP, meaning that it is going directly to the source pool.ntp.org for time (not a DC/PDCE) even though it is a domain member.
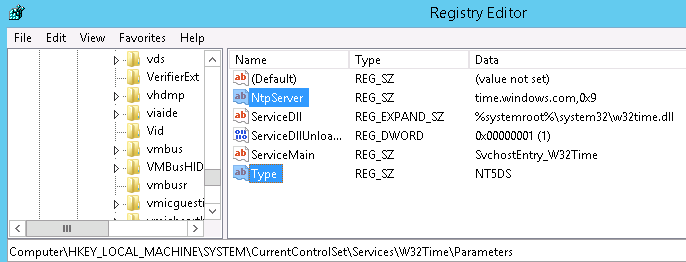
In the following example, the domain member is synchronising its time as per the domain hierarchy outlined at the top of this page. This is indicated as a Type of NT5DS. In this case the NtpServer time.windows.com is not used.
A value of AllSync in Type means the client uses the directory first for time synchronisation and then will fall back to the value set for the NTP server.
Configuring your forest root PDC Emulator to connect to an external NTP source(s)
The first thing to do is disable time sync if the machine is a VM inside Hyper-V. Open VM settings -> Management -> Integration Services and un-check Time Synchronization.
Because the PDCE role can potentially shift from one DC to another, it's most suitable to apply the NTP settings using Group Policy. First, create a WMI filter to target ONLY the domain controller that has the PDCE role.Select * from Win32_ComputerSystem where DomainRole = 5
Create a new GPO, apply the above WMI filter, and link the GPO to your domain controllers OU. Then edit the GPO and go to: Computer Configuration\Administrative Templates\System\Windows Time Service\Time Providers then Configure Windows NTP Client + Enable Windows NTP Client.
Enable the setting, change the type to NTP, and then enter your primary NTP source and then the fall-backs. The primary source should have a hex code of 0x9, and fall-back sources should be 0xa. Separate them with a space. More information on the meaning of the Hex codes can be found here.
Once group policy applies you can confirm the new NTP sources from the PDCE by typing:
w32tm /query /peers