Windows Bible
set uShow's who you are, similar to whoami in Unix.
Confirm which applications are installed and uninstall a program
wmic
product get name - this will generate a list of installed applications.
product where name="Adobe Reader 9" call uninstall - substitute Adobe Reader 9 with the name of the program as listed earlier.
wmic cpu get loadpercentage - show's the current CPU utilisation.
tasklist - shows active processes.
taskkill /F /pid 888 - forces a process with a PID of 888 to close.
tasklist /FI "imagename eq skype.exe" - shows info on a particular process, replace skype.exe with the name of the process outlined in tasklist.
ver - equivalent to uname in Unix.
Services
To start a service, type: net start service
To stop a service, type: net stop service
To pause a service, type: net pause service
To resume a service, type: net continue service
To list all running services type net start
You can also use sc to manage services.
sc query type= service - shows running services.
sc query type= service state= inactive - shows defined services that are not running.
sc query type= service state= all - shows both running and stopped services.
ipconfig /all - shows network address info including IP and MAC.
ipconfig /flushdns - flushes dns resolver cache.
sigverif - launches a program that looks for unsigned drivers that are in use. Unsigned drivers can cause blue screens.
Mapping a network drive
net use k: \\bunny\temp
K would be the drive letter added to your computer.
bunny= is the network computer name
temp= is the shared folder on the computer named bunny
You can also provide username and password details when attempting to map a drive:
net use * \\hostname\c$ /user:admin password
How to fix the Master Boot Record (MBR)
If you need to fix the MBR. I would follow these steps:
I recommend the bootrec command.
First try bootrec /fixmbr then try bootrec /fixboot
Then, if that doesn't work, try rebuilding the BCD.
cd c:\boot attrib bcd -s -h -r ren c:\boot\bcd bcd.old bootrec /RebuildBcd
Boot from the Windows DVD > REPAIR > COMMAND PROMPT and type:
DISKPART
LIST DISK
SELECT DISK N (N represents the disk you want).
LIST PARTITION
SELECT PARTITION N (N represents the partition you want).
ACTIVE
EXIT
Windows 7 startup folder location
C:\Users\username\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
How to uninstall/reinstall the SCCM client on a workstation
Open a CMD prompt as admin.
cd C:\Windows\ccmsetup
ccmsetup.exe /uninstall
A process named 'ccmsetup.exe' will now appear in tasklist.
This uninstallation process will remove a bunch of files from the 'C:\Windows\CCM' directory ('C:\Windows\SysWOW64\CCM' for 32-bit clients).
To reinstall the client type the below command from the 'C:\Windows\ccmsetup' directory:
ccmsetup.exe /mp:insert_sccm_server_name SMSSITECODE=AUTO
The client may take some time to reinstall. This whole process can be done remotely using PsExec.
Excel Error: There was a problem sending the command to the program
Microsoft Excel 2010
1.Click the File tab, and then click Options.
2.Click Advanced, and then click to clear the Ignore other applications that use Dynamic Data Exchange (DDE) check box in the General area.
3.Click OK.
Obtain a remote PCs IP address and other info:
nbtstat -a 3jspd2s
Obtain a remote PCs currently logged on user:
WMIC /NODE: xxx.xxx.xxx.xxx COMPUTERSYSTEM GET USERNAME
xxx.xxx.xxx.xxx. = IP address
How to enable a PC for remote logging
run a power shell as admin and type:
enable-psremoting
to login from ur comp type:
enter-pssession Server01
to exit type:
exit-pssession
How to check for windows updates
C:\Windows\system32\wuauclt.exe /detectnow
systeminfo
Typing systeminfo brings up detailed information about a computer. You can extract certain types of info from systeminfo by using pipe.
To find out when windows was installed:
systeminfo | find /i "install date"
To find out how much physical memory is installed:
systeminfo | find /i "total physical memory"
To run systeminfo on a remote PC:
systeminfo /S hostname
To list all groups that a user is a member of and export the result to a text file, type:
net user username /domain > filename.txt
To list all members of a group (Global/Universal) and export the result to a text file, type:
net group "group_name" /domain > filename.txt
To list all members of a group (Domain local) and export the result to a text file, type:
net localgroup "group_name" /domain > filename.txt
How to copy text in command prompt
1. Right-click on the command prompt window and select mark
2. select the text.
3. control c to copy the text.
How to tell if your CPU is 32 or 64 bit
wmic OS get OSArchitecture
Show detailed info about a user
net user username /domain
Finds any files on c drive with a size greater than 200mb.
forfiles /P C:\ /M *.* /S /D +"01/01/2012" /C "cmd /c if @f size gtr 209715200 echo @path @fsize @fdate @ftime
Show when your account password needs to be changed + other info
net user /domain username
Script that shows when a password expires and hides the commands
@ net user /domain %USERNAME% | find "Full Name"
@ net user /domain %USERNAME% | find "User name"
@ net user /domain %USERNAME% | find "Password last set"
@ net user /domain %USERNAME% | find "Password expires"
@ net user /domain %USERNAME% | find "Account active"
@echo.
@echo If your password has expired and your account is inactive, type 'Ctrl + Alt + Delete' and click on the 'Change a password...' button to reset your password.
@echo.
@ pause
Show the status of network drives.
net use
Windows file permissions explained
http://technet.microsoft.com/en-us/library/dd349321(v=ws.10).aspx
How to see all currently mapped drives:
wmic logicaldisk get name
Get Last Logged On User From Registry
Windows 7
Key: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI
Value: LastLoggedOnUser
You can do this remotely in regedit - connect network registry
How to run the command prompt as another user:
runas /user:username@domain cmd
runas /user:administrator cmd
How to remove/add a user from a local group
net localgroup "administrators" domain\username /delete
net localgroup "administrators" domain\username /add
How to remove/add multiple users from a domain group
net group "test_n_Beare" /domain username1 username2 /add
How to delete/add groups
net localgroup test_beare /add
net localgroup test_beare /delete
Host file location, can be used instead of DNS
C:\Windows\System32\drivers\etc\hosts
How to logon automatically in Windows XP and Windows 7
Click Start, and then click Run.
In the Open box, type control userpasswords2 (in Windows 7 type control userpasswords2), and then click OK.
Clear the "Users must enter a user name and password to use this computer" check box, and then click Apply.
In the Automatically Log On screen, type the password in the Password box, and then retype the password in the Confirm Password box.
Click OK to close the Automatically Log On screen, and then click OK to close the User Accounts screen.
Windows shutdown commands
shutdown -r -f -t 600 -c "haha" - forces a computer to restart in 600 seconds with a comment of "haha"
-s = shutdown
-r = restart
-f = force
-t = time in seconds
-c = comment
/l = logoff
/a = abort system shutdown
/m computer name = speciy target computer
Note, When using shutdown in a bat file, you need to specify the fullname shutdown.exe
How to find a MAC address using getmac
getmac /s 3jspd2s - get mac address for remote computer
PsEXec
Execute a program remotely:
PsExec.exe \\6jspd2s -i "C:\Program Files (x86)\Microsoft Office\Office14\POWERPNT.EXE"
Can also use username/password:
PsExec.exe \\6jspd2s -i –u username –p password "C:\Program Files (x86)\Microsoft Office\Office14\POWERPNT.EXE"
Run command prompt on a remote machine:
PsExec.exe \\hostname cmd.exe
Telnet
To begin a Telnet sessions type:
telnet
o
remote_host_name
To end the telnet session:
Hold down 'Ctrl' and push the ']' key
quit
enter
Note, telnet data is transmitted in plain unencrypted text.
Help! My network drive files are inaccessible, I can see them, but they are opaque and have a cross through them
This problem can affect a user's personal mapped drive. To fix the issue go to:
Control Panel > Sync Center > Manage Offline Files. Ensure that 'Disable offline files' is set. Then get the user to log off and try again.
How to add programs to the W7 start menu
Files in this directory will appear under Start Menu > All Programs:
C:\ProgramData\Microsoft\Windows\Start Menu\Programs
How to enter/update a Windows activation key from the cmd line
slmgr.vbs -ipk XXXXX-XXXXX-XXXXX-XXXXX-XXXXX
List installed software on a PC
wmic product get name,version
You can redirect the output to a text file
wmic /output:C:\InstallList.txt product get name,version
List installed updates (patches) on a PC
wmic qfe
You can redirect the output to a text file
wmic /output:C:\file.txt qfe
How to add the AD snap-in in Windows 7
Go to: Control Panel > Programs and Features
Under 'Turn On/Off Windows Features' select:
Remote Server Administration Tools
AD DS and AD LDS Tools
AD DS Tools
Tick AD DS Snap-ins and Command-line Tools and click OK.
AD should now appear with the rest of your administrative tools.
How to tell which domain controller authenticated your logon credentials
echo %LOGONSERVER%,
List installed programs from the command line
wmic product get name
Uninstall a program from the command line
wmic product where name="Microsoft Visio Viewer 2010" call uninstall
Install a program from the command line
msiexec
eg msiexec /I install.exe /qn /norestart
Windows equivalent to UNIX pwd command
Echo %CD%
Display the path variable
echo %PATH%
Robocopy
The below command copies the contents of c:\robocopy to a destination directory named c:\test.
robocopy C:\robocopy C:\test -copyall –e /LOG:c:\robo_log.txt
- The –copyall parameter copies ALL file info (D=Data, A=Attributes, T=Timestamps. S=Security=NTFS ACLs, O=Owner info, U=auditing info).
- The –e parameter copies all child directories of c:\robocopy even if they are empty.
- The final part of the command /LOG:c:\robo_log.txt, creates a log of the action. In this example the log was saved to c:\robo_log.txt.
To bring up a detailed help section on Robocopy type:
robocopy /?
Note, you can specify UNC paths in the source/destination locations eg \\server\share\path
Logon tricks
To log onto your local machine use a username that begins in dot backslash eg .\nick
To log onto a different domain use domain\username eg nick.com\nick
How to pause a script
Use the 'timeout' command to to pause your scripts (similar to sleep in Linux). /T specifies the desired sleep time (in seconds), and /NOBREAK means that the user needs to type control c to break the sleep.
TIMEOUT /T 300 /NOBREAK
Automatic Private IP Addressing (APIPA)
APIPA is a Windows OS feature that allows DHCP clients to automatically self-configure an IP address and subnet mask when a DHCP server isn't available. APIPA uses an IP address from a reserved range of 169.254.0.1 through 169.254.255.254 (class B).
The APIPA service checks regularly for the presence of a DHCP server. If it detects a DHCP server on the network, APIPA stops, and the DHCP server replaces the current APIPA networking address with a dynamically assigned address.
How to measure directory size
Disk Usage (du.exe), written by Mark Russinovich, is a useful tool that you can download from the web. It allows you to calculate the total size of a directory. The below command runs du.exe and lists the total size of each directory in the c:\users directory. It also includes the total size of all child folders (-v switch). Size is reported in Kilobytes (CurrentFileSize). This can be converted to Megabytes by dividing the total by 1024. Divide by a further 1024 to convert to Gigabytes. The output of the command is comma deliminated (-c switch) so it can be easily pasted into a spreadsheet.
du.exe -c -v c:\users > c:\output_file.txt
How to tell what group policy is being applied to your computer or user account
In Windows 7 type the below commands. When running the commands on Windows XP exclude the -r switch.
To show the current group policy applied to your computer/user accounts:
gpresult -r
If you only want to see the GPO affecting your computer account type:
gpresult -r /SCOPE computer
Group Policy refresh intervals
Within RSOP you can check how often your computer and user GPO is refreshed (RSOP pathways below). The default GPO refresh interval is 90 minutes for both user and computer policy.
Computer Configuration\Administrative Templates\System\Group Policy\Group Policy refresh interval for computers.
User Configuration\Administrative Templates\System\Group Policy\Group Policy refresh interval for users
How to test an SMTP server using Telnet
You will need the hostname of the target mail server. You can get this by querying the MX records of the domain.
nslookup -query=mx target_domain.com
Next, use telnet to verify that SMTP is operating on the target mail server.
telnet mail.domain.com 25
Where are the Exchange 2010 OWA login attempts stored?
They should be in the below directory on the Exchange server:
C:\inetpub\logs\LogFiles\W3SVC1
A beginner's guide to Group Policy on TechNet
http://technet.microsoft.com/en-us/library/hh147307%28v=ws.10%29.aspx
Wake on LAN with MC-WOL
Download the freeware MC-WOL program and then reference it using the below command to turn on a computer that supports WOL. Note, you will need to know the MAC address of the target computer.
c:\mc-wol.exe 00:1E:C9:81:7A:4A
In some environments you will also need to specify the IP address.
c:\mc-wol.exe 5c:f9:dd:73:d0:95 /a 192.168.232.81
The Server Configuration utility (Sconfig)
sconfig provides a text-based menu system that makes it easy to do the following:
Configure domain or workgroup membership
Change a server's name
Add a local Administrator account
Configure remote management features
Configure Windows Update settings
Download and install Windows updates
Enable or disable Remote Desktop
Configure network settings for TCP/IP
Configure the date and time
Log off, restart, or shut down
Type sconfig at the command prompt and then type the number that corresponds to the action that you want to perform.
Display the List of Authorized Servers in Active Directory for the Current Domain
netsh dhcp show server
Using ldifde to export OU structure from AD
The below command will export your current OU structure to an .ldf file. -f specifies the destination file, -s is the DC, -d is the distinguished name of the domain.
ldifde -f c:\stuff\exportOu.ldf -s DC01 -d "dc=BHP,dc=corporate" -p subtree -r "(objectCategory=o rganizationalUnit)" -l "cn,objectclass,ou"
To import the OU structure to another domain use the below command. -f specifies the input file, -s is the destination DC, -j outputs the log file to a location. Note the -k flag is very important; it ensures that errors such as parent OUs not existing, are ignored.
ldifde -i -f c:\ExportOU.ldf -s DC02 -j c:\output_location\ -k
Connecting your local hard drive to a remote server using MSTSC
Fire up MSTSC and click 'Show Options'.
Click the 'Local Resources' tab.
Click the 'More' button.
Expand 'Drives'.
Select the appropriate drive eg C:
Install Windows features from the command prompt using DISM
Type the following command to list all of the features available in the operating system.
Dism /online /Get-Features
Optional: Type the following command to list information about the specific feature you are interested in.
Dism /online /Get-FeatureInfo /FeatureName:Hearts
Type the following command to enable a specific feature in the image.
Dism /online /Enable-Feature /FeatureName:Hearts
Type the following command to disable a specific feature in the image.
Dism /online /Disable-Feature /FeatureName:Hearts
Uninstall/Install Windows Updates (KBs) from the command prompt using WUSA
To uninstall update KB980302 the command will be following.
wusa /uninstall /kb:980302
To install the update quietly in the background without a restart type the below.
wusa.exe c:\stuff\Windows6.1-KB958830-x64-RefreshPkg.msu /quiet /norestart
Show AD group membership for the current user
whoami /all
How to hide a Windows Share
End the share name with a $ symbol eg G_Drive$. It will now be hidden from users when they navigate to the host using Windows Explorer. Users will need to reference the entire share path to view the share within Windows Explorer.
How to log onto a Windows server that already has the maximum number of users logged on remotely
Use the 'Mstsc /admin' switch to force your logon. This will not log off any existing users.
How to open the Local Policy Editor
Run the below command as admin:
gpedit.msc
Public Google DNS Servers
Public DNS is a free, global Domain Name System (DNS) resolution service, that you can use as an alternative to your current DNS provider. 8.8.8.8 and 8.8.4.4.
Embed a form within a HTML web page
Note, you can change the height and width variables to set how much space the embed form uses.
<iframe src='form.php' frameborder='0' width='100%' height='600' allowtransparency='true'></iframe>
Active Directory replication
Use the Active Directory Sites and Services snap-in to force replication between DCs. Expand Sites > Your Site Name > Servers > Expand the Server you want to replicate > NTDS Settings. Now right click on 'automatically generated' and select 'Replicate Now'.
To check the current DC replication time, open Active Directory Sites and Services > Sites > Inter-Site Transports > IP. In the right hand side panel you can now see the Replication Interval of the site links.
Setting up a one way domain trust
You can configure a one way domain trust between Domain A and Domain B. This will allow Domain A to access Domain B, but Domain B will not be able to access Domain A.
Before creating the trust, open DNS Manager on Domain A. Right click on Conditional Forwarders and select New Conditional Forwarder. Add Domain B.
Next, open Active Directory Domains and Trusts on Domain A. Right click on your domain name and select properties. Click on the Trusts tab and then New Trust. To set the one way trust you will need to make sure the trust is not 'transitive'. Follow the prompts.
Preventing a user from viewing the Global Address List (GAL)
Create a security group and add the user whom you want to block from accessing the GAL. On the mail server open ADSI Edit. Right click on ADSI Edit and select 'Connect to'. Tick 'Select a well known Naming Context' and select 'Configuration'. Right click on the following location and select properties: 'CN=All Global Address Lists,CN=Address Lists Container,CN=nickbeare,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=nickbeare,DC=com'. Open the security tab and add the security group you made earlier. Deny all access to the group.
Enable GPO logging and tracing
In Group Policy Mgt Editor drill down to: Computer Configuration > Policies > Administrative Templates > System > Group Policy > Logging and tracing.
Enable the relevant logging and tracing ie for shortcuts, network shares etc. Make sure you set tracing to on. Tracing will now log the results of the GPO application under c:\ProgramData\GroupPolicy\Preference\Trace
Creating a shortcut using GPO preferences
To create a shortcut on a user's computer to a UNC path, select URL as the Target Type. Under target URL specify file:\\unc_path\goes_here\somefile.bat
Add an entry to a user's path variable
Prior to changing the path variable, type set and take a record of the user's current variables. The below line adds c:\cool and c:\stuff to the path variable universally.
setx PATH "%PATH%;c:\stuff;c:\cool" /m
You need to reopen a new cmd prompt to verify the new output of path
Using ICACLS to change the permissions of a folder including all subfolders and files
The below command grants the domainadmins group full access to \\hostname\folder and all subfolders and files.
ICACLS \\hostname\folder /grant domainadmins:F /T
Set the command prompt title for bat file output
@ TITLE Insert_Page_Title_Here
Using slmgr to configure KMS
You need a KMS server with a KMS host key installed. This server will need to receive either 25 workstation activation requests or 5 server requests before it will activate clients. You can simulate KMS client requests using a KMS client emulator. A list of KMS client keys (GLVK) can be found at technet.
slmgr /skms hostname:1688 - sets the KMS server destination as hostname on port 1688
slmgr /ipk insert_activation_key_here - register activation key on client.
slmgr /ato - activate the KMS client key via the KMS host.
slmgr /dlv - shows general info on the client or host.
slmgr /xpr - show trial period expiration date.
slmgr /rearm - extend trial period expiration date.
CSVLK are KMS-host keys, for on-line (or phone) activation throigh MS. Each key can activate 6 different machines, real or virtual. Machines, activated with CSVLK keys, become KMS-hosts and can activate clients if they use GVLK key.
rmdir
The below command will remove a folder recursively, including files with names exceeding 256 characters.
cmd /C "rmdir /S c:\folder"
Takeown
The below command assigns Administrator as the owner of the nominated folder, including all child folders and files.
takeown /a /r /d Y /f c:\folder
Deleting files with DEL
You can delete one or more files using DEL. The below command deletes the extend.dat file.
DEL C:\Users\%USERNAME%\AppData\Local\Microsoft\Outlook\extend.dat
Editing the registry
The top level in the registry such as HKEY_CURRENT_USER is referred to as the hive. You can export a registry key, including all values, by right clicking on it in regedit.exe and selecting 'Export'.
You can script changes to the registry by creating a simple bat file that links to a .reg file which contains the exported key.
Bat file:
regedit /s registry_file.reg
The .reg file needs to include the below in the top line:
Windows Registry Editor Version 5.00
You can then include your exported reg keys eg:
[HKEY_CURRENT_USER\Software\Microsoft\Office\Outlook\Addins\HP.HPTRIM.Outlook.Addin.AddinModule]
"CommandLineSafe"=dword:00000000
Clear your DNS cache
ipconfig /flushdns
Show your current logon server (DC)
echo %logonserver%
In PowerShell:
get-childitem env:logonserver
Show all operational DCs in the domain
dsquery server
Show all active logon sessions on a machine, including RDP sessions
Show RDP sessions on local machine:
qwinsta
Show RDP sessions on remote server. Note the ID of the session:
qwinsta /server:server_name
Close an RDP session on a remote server based on the user's session ID. I have used 2 in the below example:
rwinsta 2 /server:server_name
nslookup equivalent using ping
ping -a ipaddress_or_hostname
How to check if RDP is blocked
You can telnet to the host and specify the RDP port 3389.
telnet 192.168.242.102 3389
Shows files opened remotely via local share points
Run the below as admin:
openfiles
SQL install guide
Show current working directory in cmd prompt
chdir is the cmd prompt equivalent to pwd or get-location.
Removing cached group policy on a workstation
Clear out the below dir:
C:\ProgramData\Microsoft\Group Policy\History
Wipe a disk using DISKPART
Type the below in a cmd prompt:
DISKPART
LIST DISK
SELECT DISK N (N represents the disk you want)
Clean
(remove all partition and volume info from the hard drive)
Manipulating licence key information for MS Office
Open a cmd prompt and change dir to the relevant Office directory eg for a 32 bit version of Office 2010 - C:\Program Files(x86)\Microsoft Office\Office14
View status of all office licence keys:
cscript ospp.vbs /dstatusall
Activate office licence keys:
cscript ospp.vbs /act
Show KMS activation events:
cscript ospp.vbs /dhistorykms
Set KMS host and port:
cscript ospp.vbs /setprt:1688
cscript ospp.vbs /sethst:KMS_Hostname
Share and folder permissions
It is best practice to open shares to as many users as possible, but to tightly lock down folders within the share using NFTS permissions. This is because share permissions overwrite child folder NTFS permissions. For example a user who has full control over a folder via NTFS permissions will not be able to even read the folder if they do not have at least read access to the share containing the folder.
Batch script that puts a computer to sleep
@echo off
powercfg -h off
rundll32.exe powrprof.dll,SetSuspendState 0,1,0
powercfg -h on
Batch file that locks the screen
@ "C:\Windows\System32\rundll32.exe" user32.dll, LockWorkStation
Open Programs and Features as administrator
Open a command prompt as admin and type:
appwiz.cpl
Removing applications using MSIExec
You can uninstall applications that were installed using MSIs by following the below steps.
Open regedit.exe and navigate to the below locations. Search the hive for the desired application name.
For 32 bit apps:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall
For 64 bit apps:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
Copy the 'UninstallString' into a command prompt. It should look like the below. Once you execute the command the uninstall process will commence.
MsiExec.exe /X{01CC2860-A3CD-4D57-98A5-B202CA6B04ED}
How do you map a printer using Group Policy Preferences?
Open Group Policy Management Editor and go to:
User Configuration > Preferences > Control Panel Settings > Printers
Right click > New > Shared Printer
Action = Update
Type in the share path of the printer.
How to map a drive using pushd
pushd "\\UNC_path\share"
How to add the AD Schema snap-in
Open a cmd prompt and type:
regsvr32 schmmgmt.dll
Where the DNS configuration files are found
c:\windows\system32\dns
Show which servers are hosting the FSMO roles
netdom query fsmo
Joining a workstation to the domain from the cmd line
To join mywksta to the devgroup.contoso.com domain in the Dsys/workstations OU, type the following command at the command prompt:
netdom join /d:devgroup.contoso.com mywksta /OU:OU=Dsys,OU=Workstations,DC=devgroup,DC=contoso,DC=com
Besides adding the computer account to the domain, this command modifies the workstation to contain the appropriate shared secret to complete the Join operation
Outlook Nickname files
Office 2007 users have their cached email addresses stored in a .NK2 nickname file within their app data folder (C:\Users\pbearen\AppData\Roaming\Microsoft\Outlook). However, Outlook 2010 saves the nickname file within the user's mailbox on the Exchange server. This means they can log onto any computer and access their entire nickname history, and you don't have to worry about backing it up when re-profiling.
Uninstall msi files based on program name
wmic product where "name like '%program_name%'" call uninstall /nointeractive
Note, before running the above command, you should run the below command to check what software you will remove.
wmic product where "name like '%program_name%'"
HTML non-breaking space
The below HTML code can be used to insert a non-breaking space:
 
To enter viewable code on a HTML page just use the code tags.
Controlling services via regedit32
To identify services:
services.msc names services according to their Description (refer to Task Manager > Services).
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services names services according to their Name (refer to Task Manager > Services).
To manipulate services:
To edit the start-up preference of a service via the registry, navigate to the above hive and click on the desired service. Edit the Start DWORD value. 2 = automatically start the service, 4 = disable the service, 3 = will not start the service on next reboot until the user manually starts it.
Using EventCombMT to diagnose account lockouts
The EventCombMT utility is included in the Account Lockout and Management Tools download (ALTools.exe).
To search the event logs for account lockouts, follow these steps:
1.Start EventCombMT.
2.On the Options menu, click Set Output Directory, select an existing folder, or click New Folder to create a new folder to save the output to, and then click OK.
Note If you do not specify an output directory, the default location is C:\Temp.
3.On the Searches menu, point to Built In Searches, and then click Account Lockouts.
All domain controllers for the domain appear in the Select To Search/Right Click To Add box. Also, in the Event IDs box, you see that event IDs 529, 644, 675, 676, and 681 are added.
4.In the Event IDs box, type a space, and then type 12294 after the last event number.
5.In the Options menu, select Set Date Range.
6.In the From box, choose your start date and time.
7.In the To box, choose your end date and time, and then click OK.
8.Click Search.
9.To search other computers (non-domain controllers) for account lockout events, right-click the Select To Search/Right Click To Add box, and then click Remove Selected Servers From List. To add computers to search, right-click the Select To Search/Right Click To Add box, and then click one of the options. For example, to add computers one at a time, click Add Single Server. Click the server or servers that you want to search, and then click Search.
To determine what the HEX codes mean for the 675 events (Pre-authentication failed, ie 0x18 usually means a bad password attempt), refer to this page.
RDP session statuses explained
Active - a user is active within a remote desktop session, for example, running applications, web browsing or similar stuff that involves using a mouse or keyboard.
Idle - User is considered idle after a period of mouse/keyboard inactivity in the RDP session. The user will be considered idle if there is no activity (e.g. keyboard strokes or mouse movement) in the configured time period. The default Terminal Services idle timeout is 1 minute, and the default for the Terminal Services Log is 5 minutes.
Disconnected - When a user is disconnected from the session but the session is still running. User could have been disconnect due to network or other failure or did not use proper log out procedure and just closed the Remote Desktop session window with the Close button [x]. This session is still running on the server and consuming resources, the users can reconnect and resume their disconnected session.
From within a cmd prompt, open another cmd prompt in a new window
start cmd
Run task manager from cmd prompt
taskmgr
Allowing ping and RDP through the Windows Firewall
For RDP, allow the below pre-defined inbound rules:
Remote Desktop - User Mode (TCP-In)
Remote Desktop - User Mode (UDP-In)
To allow pings:
File and Printer Sharing (Echo Request - ICMPv4-In)
Exchange 2010 installation and configuration guide
Installation guide
Configuration guide
Permit incoming mail from external users - In the Exchange Management Console go under your Server configuration, hub transport server default receive connector, properties, click on last tab permission Groups place check mark into Anonymous users click apply and ok.
Write debugging information
Go to Advanced System Settings (alt + pause break) > System properties > Advanced tab > Under Startup and Recovery click settings. Set Write debugging information to Kernal memory dump with a dump file of %SystemRoot%\MEMORY.DMP (which is C:\Windows). There are some other settings here like automatically restarting after a bluescreen and overwriting the existing dump file.
Debugging Tools for Windows (WinDBG)
You can install the SDK from the Microsoft website. When you open the tool import user symbols by going to File, Symbol File Path. Enter a path of:
SRV*c:\symbols*http://msdl.microsoft.com/download/symbols
Now close and reopen the application. To investigate a blue screen dump go to File, Open Crash Dump. Open the below dump:
C:\Windows\MEMORY.DMP
Click on the analyze link to view more info about the blue screen event. The most useful info is the IMAGE_NAME and MODULE_NAME at the bottom, which indicate the process that caused the blue screen event.
Force a blue screen event so you can check that debugging is working
Modify the registry by running the below reg file as an administrator. You will then need to restart the PC. After the restart you can force a blue screen event by holding one of the control keys and hitting scroll lock multiple times.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\kbdhid\Parameters]
"WorkNicely"=dword:00000000
"CrashOnCtrlScroll"=dword:00000001
Diagnosing account lockouts
When combing the security event log for logon events you will come across the below Logon Types.
Logon Type: 2 = Interactive
A user attempts to log on at the local keyboard and screen with a domain account or a local account. To tell the difference between an attempt to logon with a local or domain account look for the domain or computer name preceding the user name in the events description.
Logon Type: 3 = Network
When you access a computer from elsewhere on the network. One of the most common sources of logon events with logon type 3 is connections to shared folders or printers.
Logon Type: 4 = Batch
A scheduled task run as a specified user account.
Logon Type: 5 = Service
A service configured to run as a specified user account. Failed logon events with logon type 5 usually indicate the password of an account has been changed without updating the service
Logon Type: 7 = Unlock
When a user returns to their workstation and unlocks the console.
Logon Type: 8 = NetworkCleartext
A network logon like logon type 3 but where the password was sent over the network in clear text.
Logon Type: 9 = NewCredentials
If you use the RunAs command to start a program under a different user account and specify the /netonly switch, Windows records a logon/logoff event with logon type 9.
Type 10 = RemoteInteractive
When you access a computer through Terminal Services, Remote Desktop or Remote Assistance windows logs the logon attempt with logon type 10 which makes it easy to distinguish true console logons from a remote desktop session.
Type 11 = CachedInteractive
Windows supports a feature called Cached Logons which facilitate mobile users. When you are not connected to the organizations network and attempt to logon to your laptop with a domain account theres no domain controller available to the laptop with which to verify your identity. To solve this problem, Windows caches a hash of the credentials of the last 10 interactive domain logons. Later when no domain controller is available, Windows uses these hashes to verify your identity when you attempt to logon with a domain account.
Group Policy location for account lockout policies
Includes policies such as enforcing account lockouts after a certain number of incorrect password attempts.
Computer Configuration\Windows Settings\Account Policies\Account Lockout Policy
Port numbers
0 to 1023 are the well-known ports. They are used by system processes that provide widely used types of network services.
The range of port numbers from 1024 to 49151 are the registered ports. On most systems, registered ports can be used by ordinary users.
The range 49152-65535 is used for custom or temporary purposes.
Run mstsc from the command line and specify the RDP port
MSTSC /v:192.168.0.150:3390
Change the default RDP port of 3389 to a non-standard port number
Run Regedit and go to this key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
Find the "PortNumber" subkey and notice the value of 00000D3D, hex for (3389). Modify the port number in decimal and save the new value.
Windows Explorer not showing thumbnails for images
To show pics as thumbnails in Windows explorer:
Open Folder Options and click on the view tab.
Make sure "Always show icons, never thumbnails" option is not enabled.
Program to recover deleted files
Recuva - http://www.piriform.com/recuva
Website that installs multiple popular software applications easily
NiNite - http://ninite.com/
Configuring Windows 8.1 to boot straight to the desktop (not the metro screen)
Go to:
Control panel > Personalization > Taskbar and Navigation > Navigation tab > tick the checkbox "When I sign in or close all apps on a screen, go to the desktop instead of start"
Securing RDP
You can perform the below steps to tighten the security of RDP:
Change the RDP default port number - Change the default RDP port of 3389 to a non-standard port number. Run Regedit and go to this key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
Find the "PortNumber" subkey and notice the value of 00000D3D, hex for (3389). Modify the port number in decimal and save the new value. Remember to add an inbound firewall rule to allow the new RDP port.
Protect from man in the middle attacks - When enabling RDP tick the "Allow connections only from computers running Remote Desktop with Network Level Authentication" checkbox. It's not a necessity to require Network Level Authentication, but doing so makes your computer more secure by protecting you from Man in the Middle attacks.
Specify accounts that can use RDP - Go to the Start menu or open a Run prompt (Windows Key + R) and type 'secpol.msc' to open the Local Security Policy menu. Once there, expand 'Local Policies' and click on 'User Rights Assignment'. Double-click on the 'Allow log on through Remote Desktop Services' policy listed on the right. Remove both of the groups already listed in this window, Administrators and Remote Desktop Users. After that, click 'Add User or Group' and manually add the users you'd like to grant Remote Desktop access to.
Encrypt the RDP traffic - open the Local Group Policy Editor by typing 'gpedit.msc' into either a Run prompt or the Start menu. When the Local Group Policy Editor opens, expand Computer Policy - Administrative Templates - Windows Components - Remote Desktop Services - Remote Desktop Session Host, and then click on Security. Set client connection encryption level - Set this to High Level so your Remote Desktop sessions are secured with 128-bit encryption. Require secure RPC communication - Set this to Enabled. Require use of specific security layer for remote (RDP) connections - Set this to SSL (TLS 1.0). Require user authentication for remote connections by using Network Level Authentication - Set this to Enabled.
Monitor RDP login attempts - Open Event Viewer, expand Applications and Services Logs - Microsoft - Windows - TerminalServices-LocalSessionManger and then click Operational. Click on the events to see login information.
Export RSOP in html format (looks like group policy management settings)
gpresult /h:"c:\RSOP.html"
Sysprep
The System Preparation (Sysprep) tool prepares an installation of Windows for duplication.
Duplication, also called imaging, enables you to capture a customized Windows image that you can reuse throughout an organization.
The sysprep /generalize command removes unique information from your Windows installation, which enables you to reuse that image on different computers.
Sysprep location:C:\Windows\System32\sysprep\sysprep.exe
Use: sysprep /audit /generalize /shutdown
Using SUBINACL to grant users/groups permissions over services
Subinacl can be downloaded from the Microsoft Website.
Subinacl install location:
C:\Program Files (x86)\Windows Resource Kits\Tools
To execute subinacl cd to the above dir and run the below commands:
Show current permissions of a service eg spooler. Note the service 'name' is used, subinacl doesn't recognise 'DisplayName'.
.\subinacl.exe /service '\\hostname\spooler'
Grant access to start/stop/restart a service:
.\subinacl.exe /service '\\hostname\spooler' /grant="domain\username"=STOPE
Remove access from a service:
.\subinacl.exe /service '\\hostname\spooler' /revoke="domain\username"
Batch script that waits for a random amount of time
:: set a random amount of time between 1 and 100 seconds
SET /A time=%RANDOM% * 100 / 32768 + 1
:: Wait for the above time period.
timeout /T %time%
Using subinacl in a batch script or cmd prompt
Note the absence of the back ticks ‘ in the below commands. These should be stored in a batch file and run from a command prompt. The back ticks ‘ in the above command are for when running SUBINACL in powershell.
.\subinacl.exe /service \\hostname\spooler /grant="domain\group2"=STOPE
.\subinacl.exe /service \\hostname\winrm /grant="domain\group1"=STOPE
.\subinacl.exe /service \\hostname\w32time /grant="domain\username1"=STOPE
More on KMS
Show info about your DNS KMS SRV record:
nslookup -type=srv _vlmcs._tcp
Disable KMS caching:
slmgr -ckhc
Enable KSM caching:
slmgr -skhc
Clear current KMS host:
slmgr -ckms
To hard set the KMS hostname and port number on a KMS client edit the below registry hive on the client and add the below string values (REG_SZ).
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform]
"KeyManagementServiceName"="KMS_SERVER_NAME"
"KeyManagementServicePort"="1688"
How to display symbols as text in a HTML page
From left to right: symbol, description, entity name, entity number
non-breaking space  
< less than < <
> greater than > >
& ampersand & &
¢ cent ¢ ¢
£ pound £ £
¥ yen ¥ ¥
€ euro € €
© copyright © ©
® registered trademark ® ®
Manually set HD in Netflix
On a playing movie screen in Netflix hold down shift + alt and then left click. Select stream manager and specify your desired quality.
Copying files from the command line
The below batch script is used to recursively copy a folder including all child folders/files:
@echo off
xcopy /Q /Y /E "source folder" c:\destination\*.*
exit
This batch script can be use to copy a file to a newly created folder:
@echo off
mkdir C:\tools\PasswordUtils
xcopy /q /y passutils.exe c:\tools\PasswordUtils\*.*
exit
Show active DCs in your environment including the PDC
nltest /DCLIST:domain_name
Show time server (source)
w32tm /query /source
Check time difference between client and NTP server
w32tm /stripchart /computer:ntp.gov.au
Show domain information
Show FSMO roles:
netdom query fsmo
Show domain trusts:
netdom query trust
Show domain controllers:
netdom query dc
Creating a bootable USB drive using Windows
Use RUFUS
Batch script to remove an msi install
You can find the GUID for a particular program by searching in the below registry hives. Refer to the UninstallString of the program you wish to uninstall. Note you can right click and do a search on the Uninstall folder to find the desired program.
32bit apps - HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall
64bit apps - HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
@echo off
MsiExec.exe /X {81BE0B17-563B-45D4-B198-5721E6C665CD} /qn /norestart
exit
Map a drive using the first available drive letter
net use * '\\file_server\e$\shared_drive\information technologyManaging file ownership and NTFS permissions
Take ownership of the folder and its children recursively.:takeown /f '.\parent_folder' /r /d y
To set the owner as the local administrator use the /a switch:
takeown /f c:\sample_folder /a /r /d y
Grant full permission to the required account. Note that this will apply recursively:
icacls '.\parent_folder' /grant sample_username:F /t
You can also remove access recursively for users and groups:
icacls C:\tools /remove 'domain admins' /t
You can also recursively list the permissions for a folder and its children:
get-childitem -recurse c:\parent_folder | Get-Acl | Format-List -property path, owner, accesstostring
Some useful Group Policies
Change the desktop wallpaperUser Configuration - Policies - Administrative Templates - Desktop - Desktop
Desktop Wallpaper ENABLED
Set the homepage in IE
User Configuration - Policies - Administrative Templates - Windows Components - Internet Explorer
Disable changing home page settings ENABLED
Change the login wallpaper
Computer Configuration - Policies - Administrative Templates - Control Panel - Personalization
Force a specific default lock screen image ENABLED
Login in with a domain account automatically
Download the Sysinternals tool named Autologon. Run it as admin and enter the username, password and domain and it will log in with the account automatically at startup.Uninstall an MSI remotely
You can use psexec to run as local system with the -s switch and uninstall a currently installed program (msi) by referencing the original msi installer.c:\tools\PsExec.exe \\computername -s MsiExec.exe /uninstall '\\computername\c$\Mozilla Firefox 3.5.8.msi' /qn / norestart
Configuring NTP
Manually set the computer to get its time from an NTP server, in the below example pool.ntp.orgw32tm /config /manualpeerlist:pool.ntp.org /syncfromflags:manual /update
Resync the time with the NTP server:
w32tm /resync
View information about the current NTP client config eg source, last successful sync time etc
w32tm /query /status
View time source information including offest:
w32tm /monitor /domain:domain
Loopback processing
Loopback processing allows GPO user configurations to apply to computer objects. Users logging onto these computers will receive the user configurations in a merged or authoritative style:User Group Policy Loopback Processing Mode
Computer Configuration\Administrative Templates\System\Group Policy
How often does Group Policy apply to computers?
By default every 90-120 minutes.Group Policy refresh interval for computers
Computer Configuration\Administrative Templates\System\Group Policy
How to RDP to a computer when two sessions are in use
mstsc /v:192.168.1.1 /adminGroup Policy for setting proxy settings
User configuration - Preferences - Control Panel Settings - Internet SettingsGroup Policy Special Preferences
Used to edit settings such as:- Start Menu settings
- Regional and Language settings
- Internet options
- Folder options
- Power options (to include Power Schemes)
Green means the setting will be delivered and processed by the client.
Red means the setting will not be delivered or processed by the client.
Use the function keys to toggle the editing state of the above settings:
F5: Enable All
F6: Enable Current
F7: Disable Current
F8: Disable All
Open straight to Network Connections window
ncpa.cplCompile a 60 second report on the performance of your computer
Run as administrator:perfmon /report
How to install Integration Services on Hyper-V
The Integration Services are software packages that improve integration between the virtualization server (Hyper-V) and the virtual machine. A good example is that the NIC may not work after creating the Virtual Machine until you install the Integration Services. Another example is that the mouse can't move outside of the virtual machine window except when you press the Ctrl+Alt_Left Arrow keys.To install the Integration Services, from the Action menu of Virtual Machine Connection, click Insert Integration Services Setup Disk. If Autorun does not start the installation automatically, you can start it manually by navigating to the CD drive, right-clicking on it, and selecting AutoPlay.
How to run the Database Connector
Run odbcWindows operating system versions
For each version of Windows, there is a unique version number:- Windows Server 2012/Windows 8 - 6.2
- Windows Server 2008 R2/Windows 7 - 6.1
- Windows Server 2008/Windows Vista - 6.0
- Windows 2003/Windows XP 64-bit - 5.2
- Windows XP - 5.1
- Windows 2000 - 5.0
SCCM collection query
The below query will return all Windows Server 2012 clients:select SMS_R_SYSTEM.ResourceID, SMS_R_SYSTEM.ResourceType, SMS_R_SYSTEM.Name, SMS_R_SYSTEM.SMSUniqueIdentifier, SMS_R_SYSTEM.ResourceDomainORWorkgroup, SMS_R_SYSTEM.Client from SMS_R_System where SMS_R_System.OperatingSystemNameandVersion like "%Server%" and SMS_R_System.OperatingSystemNameandVersion like "%6.2%"
How to disable Java auto update using the registry
Open regedit and browse to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\JavaSoft\Java Update\PolicyAdd a DWORD Value called EnableJavaUpdate and set it to 0
Open Windows OS phone activation window
slui.exe 4Add a HTML comment
<!--This is a comment. Comments are not displayed in the browser-->Show RAM speed
From a cmd prompt type:wmic memorychip get speed
Show version of Windows
winverGive users permission to add and remove devices from a collection in SCCM 2012
On the collections: Read; Modify; Modify Resource; Delete Resource; Read Resource.And on the site: Read; Import Computers
Install software using Group Policy
Computer Configuration - Policies - Software Settings - Software InstallationRight click in the empty space and select new Package. The actual installation of the software won’t take place until the computer restarts.
Manually remove the SCCM 2012 client
1. run c:\windows\ccmsetup\ccmsetup.exe /uninstall and wait until ccmsetup disappears from taskmgr2. rd /s c:\windows\ccm
3. rd /s c:\windows\ccmcache
4. rd /s c:\windows\ccmsetup
5. del /s c:\windows\smscfg.ini
6. del HKLM\software\Microsoft\ccm
7. del HKLM\software\Microsoft\CCMSETUP
8. del HKLM\software\Microsoft\SMS\
9. del HKLM\software\Microsoft\Systemcertificates\SMS\Certificates
10. del /s c:\windows\sms*.mif (if present)
Convert a physical server to a VHD
Use the Disk2vhd sysinternals tool or System Center Virtual Machine Manager (SCVMM), although this functionality appears to have been removed in 2012 R2.How up to date is lastLogonTimestamp?
To reduce lastlogontimestamp-related replication traffic, DCs update the value only every 9 to 14 days. Whenever a DC logs you on, that DC looks at your current lastlogontimestamp value. The DC then picks a random real number between 9 and 14. If the number of days between when you last logged on and now is smaller than the random number, the DC doesn’t update your lastlogontimestamp value. As a result, each user's lastlogontimestamp value gets updated only once every 12 days or so—no matter how often that user logs on during that time period. Less precision, yes, but also a lot less replication traffic.Difference between lastlogon and lastLogonTimestamp
The lastLogon attribute stores information about the last successful user logon only on that particular Domain Controller and it is NOT replicated to other Domain Controllers. lastLogonTimestanp is replicated to other DCs.Convert lastlogon and lastLogonTimestamp to human readable date
Just replace '130517025354716586' with the relevant lastlogon or lastLogonTimestamp value.[datetime]::FromFileTime("130517025354716586")
You can also convert this in excel using the below formula where cell A1 refers to the lastlogon or lastLogonTimestamp value.
=IF(A1>0,A1/(8.64*10^11) - 109205,"")
Force AD replication using repadmin
This can also be done via the GUI in sites and services.repadmin /syncall
You can also view all site bridgehead servers using repadmin.
repadmin /bridgeheads /v
Boot Windows in Safe mode
You can boot Windows into safe mode using msconfig. This is especially useful on Win8/2012 and above systems as you cannot hit F8 at startup as you normally would with older Operatings Systems.
Batch script to add domain groups to local admin group
NET localgroup Administrators /add "domain\BasicDomainAdmins"NET localgroup Administrators /add "domain\Local Admin Users"
NET localgroup "Offer Remote Assistance Helpers" /add "domain\RemoteAssistance"
NET localgroup "Remote Desktop Users" /add "domain\BasicDomainAdmins"
Features available at forest and domain functional levels
TechnetStep by step guide for packaging exe as an application in SCCM 2012
LinkGroup Policy Preference Registry Actions Explained
Create - Create a new registry value or key for computers or users.Delete - Remove a registry value or a registry key and all of its values and subkeys for computers or users.
Replace - Delete and recreate a registry value or key for computers or users. If the target is a registry value, the net result of the Replace action is to overwrite all existing settings associated with the registry value. If the target is a registry key, the net result is to delete all values and subkeys in the key, leaving only a default value name with no data. If the registry value or key does not exist, then the Replace action creates a new registry value or key.
Update - Modify settings of an existing registry value or key for computers or users. This action differs from Replace in that it only updates settings defined within the preference item. All other settings remain as configured in the registry value or key. If the registry value or key does not exist, then the Update action creates a new registry value or key.
Group Policy Client Side Extensions for XP
KB943729Hirens Boot Disk
A boot disk that can be used to reset the local administrator password on Windows operating systems.Domain Local, Global and Universal Groups
Domain Local GroupsAny user account, global or universal group in any domain in the same forest (including trusted forests) can join this group. Note, domain local groups from other domains cannot be added.
The Domain Local Group can then be given permission over resources within the local domain only (it cannot be given access to resources outside the local domain).
Global Groups
Any user account or global group in the same domain can join this group. Global groups cannot contain objects from other domains in the same forest.
The global group can then be given permission over resources within any domain in the forest (including trusted forests).
Universal Groups
Any user account, global or universal group in the same domain can join this group, as well as global and universal groups from other domains in the same forest.
The universal group can then be given permission over resources within any domain in the forest (including trusted forests).
Show all Global Catalogs in a domain
dsquery server -isgc -domain nickbeare.comYou can also view the SRV records in DNS they start with _gc
Show FSMO roles for a domain
netdom query fsmo -domain nickbeare.comShow all DCs in a domain
netdom query dc -domain nickbeare.comMSC shortcuts
| Active Directory Rights Management Services | AdRmsAdmin.msc |
| ADSI Edit | adsiedit.msc |
| Active Directory Certificate Services | certsrv.msc |
| Computer Management | compmgmt.msc |
| DFS Management | dfsmgmt.msc |
| DHCP Console | dhcpmgmt.msc |
| Disk Management | diskmgmt.msc |
| DNS Console | dnsmgmt.msc |
| Active Directory Domains and Trust | domain.msc |
| Active Directory Users and Computers | dsa.msc |
| Active Directory Site and Subnets | dssite.msc |
| Event Viewer | eventvwr.msc |
| Group Policy Management Console | gpmc.msc |
| Group Policy Management Editor | gpme.msc |
| LDP | ldp.exe |
| PKI - Enterprise PKI | pkiview.msc |
| Resultant Set of Policy | rsop.msc |
| Server Manager | ServerManager.msc |
| WINS | winsmgmt.msc |
| WMI | WmiMgmt.msc |
| Security Policy Editor | secpol.msc |
| Terminal Services | tsmmc.msc |
| File Server Resource Manager | fsrm.msc |
Troubleshooting AD replication with repadmin
Display the highest Update Sequence Number on a serverrepadmin /showutdvec . 'dc=microsoft,dc=com' server2.microsoft.com
Display the replication partners of a server:
repadmin /showrepl server1.microsoft.com
Initiate a replication event between two replication partners:
Server2 initiates replication of the domain directory partition for microsoft.com from Server1. In this example, Server1 is the source server and Server2 is the destination server.
repadmin /replicate server2.microsoft.com server1.microsoft.com dc=microsoft,dc=com
Display the connection objects for a server:
repadmin /showconn server2.microsoft.com
Showing the replication status of a forest using replsummary and wildcard characters:
The following example uses the replsummary operation and a wildcard character to show a summary of the replication status for all the domain controllers in the forest with a name beginning with 'FOURTH'
repadmin /replsummary FOURTH*
Show detailed information about an AD object and its attributes:
SOE Tools
MDTSCCM Queries
Collection query statement that adds members who are a member of a particular AD group:select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System where SMS_R_System.SystemGroupName = "DOMAIN\\AD_Security_Group"
Custom query statement that returns computers that have particular software installed. In the below example I have used Google Chrome.:
select SMS_R_System.Name, SMS_R_System.LastLogonUserName, SMS_G_System_ADD_REMOVE_PROGRAMS.DisplayName, SMS_G_System_ADD_REMOVE_PROGRAMS.Version from SMS_R_System inner join SMS_G_System_ADD_REMOVE_PROGRAMS on SMS_G_System_ADD_REMOVE_PROGRAMS.ResourceId = SMS_R_System.ResourceId where SMS_G_System_ADD_REMOVE_PROGRAMS.DisplayName like "%google chrome%"
What is SYSVOL?
The Sysvol folder is shared on all the domain controllers in a particular domain. It is used to deliver the policy and logon scripts to domain members. These are stored in the below folders:
Policies - (Default location - %SystemRoot%\Sysvol\Sysvol\domain_name\Policies)
Scripts - (Default location - %SystemRoot%\Sysvol\Sysvol\domain_name\Scripts)
Changes to any of the policies will be committed to the assocated GUID name folder in the Policies folder and replicated to all Domain controllers.
Net use
Map a drive with spaces in the UNC path, note the use of double quotes around the location.:net use x: "\\fileserver\Shared_Drive\Finance\Employee Reports\Financial Reports" /user:DOMAIN\username insert_password_here
Remove a drive mapping:
net use x: /delete /yes
Remove all mapped drives:
net use * /delete /y
Copy all partitions from one volume to another volume
LinkFile Server Resource Manager (FSRM)
You can use FSRM to create quota templates than can impose hard or soft limits on directories.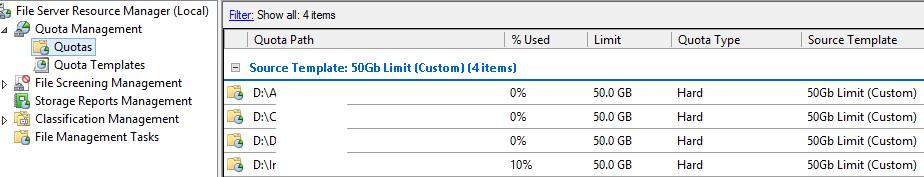
Set the default homepage in Google Chrome using Group Policy
LinkRemove a DC from an Active Directory domain
The below command assumes the default settings and assigns a new local admin password. If you don't need to do anything except remove a DC, then this command should be suitable.dcpromo /AdministratorPassword:New Local Admin Password
To see a full list of options run:
dcpromo /?:demotion
Display a list of currently cached Kerberos tickets
klistIBM IMM (Integrated Management Module) Default Username and Password
Username: USERIDPassword: PASSW0RD
Comparison of file systems
NTFS maximum filename and pathname length is 255 characters.Comparison of file systems
NIC Teaming PowerShell commands
Windows Server 2012 NIC Teaming has PowerShell cmdlets that operate on the following object types:
| Objects to be managed | Supported operations on the object |
| NetLbfoTeam | Get, New, Remove, Rename, Set |
| NetLbfoTeamMember | Add, Get, Remove, Set |
| NetLbfoTeamNic | Get, New, Remove, Set |
Show all installed product keys
cscript c:\windows\system32\slmgr.vbs /dlv allPCIe
Smaller PCIe cards can be used in larger slots ie a 1x card can fit and operate in a 1x, 4x, 8x and 16x slot. PCIe supersedes AGP, PCI and PCI-X.Removing an orphaned domain
I found the two below Microsoft KBs useful when I had to remove an orphaned child domain that I could no longer access (dcpromo was not used to decommission it). I had to remove the contents of the orphaned DC's NTDS folder from ADSIEDIT before the domain could be removed from NTDSUTIL (I couldn't remove it from AD Sites and Services).How to remove orphaned domains from Active Directory
0x2015 error in NTDSUTIL
GPO WMI Filters
The namespace for the below WMI filters is root\CIMv2.
XP WMI filter:
SELECT * FROM Win32_OperatingSystem WHERE Version like "5.1%" AND ProductType = "1"
Win7 WMI filter:
SELECT * FROM Win32_OperatingSystem WHERE Version like "6.%" AND ProductType = "1"
Hardware model eg Optiplex:
select * from Win32_ComputerSystem where Model like '%Optiplex%'
Difference between an Authoritative and Non-Authoritative restore
In short:Non-Authoritative: Non-Authoritative method will restore an active directory to the server in which the restore is being done and will then receive all of the recent updates from its replication partners in the domain.
Authoritative: Authoritative method restores the DC directory to the state that it was in when the backup was made, then overwrites all the other DC's to match the restored DC.
In long:
Non-Authoritative: The default Directory Services restore mode is a nonauthoritative restoration. In this mode, Windows restores a DC's directory from the backup. Then, the DC receives from its replication partners new information that's been processed since the backup. For example, let's say we restore a DC using a 2-day-old backup. After the DC starts, its replication partners send all updates that have occurred in the past 2 days. This type of restore is typically used if a DC fails for hardware or software reasons.
Authoritative: An authoritative restoration restores the DC's directory to the state it was in when the backup was made, then overwrites all other DCs to match the restored DC, thereby removing any changes made since the backup. You don't have to perform an authoritative restoration of the entire directory--you can choose to make only certain objects authoritative. When you restore only parts of the directory, Windows updates the rest of the restored database by using information from the other DCs to bring the directory up-to-date, then replicates the objects that you mark as authoritative to the other DCs. This type of restore is most useful if you deleted, for example, an organizational unit (OU). In this case, you could restore an AD backup to a DC, mark the OU as authoritative, then start the DCs normally. Because you marked the OU as authoritative, Windows will ignore the fact that the OU was previously deleted, replicate the OU to the other DCs, and apply all other changes made since the backup to the restored DC from its replication partners.
Display the contents of the client DNS Resolver Cache
ipconfig /displaydnsSet the NTP source on the PDC Emulator using Group Policy
Set a WMI filter to target only the PDC emulator:Select * from Win32_ComputerSystem where DomainRole = 5
Create a GPO, link it to the Domain Controllers OU (with the above WMI filter) and make the required changes to:
Computer Configuration\Administrative Templates\System\Windows Time Service\Time Providers then Configure Windows NTP Client + Enable Windows NTP Client
Show serial number
wmic bios get serialnumberHow to count lines of output
The find command can be used to count the number of lines of output. The below command returns the total number of lines of output from the systeminfo command. It's like using wc -l in Linux. Note this only seems to work in cmd.exe, not PowerShell.systeminfo | find /c /v ""
Redirect new computer and user objects
Change the default container for newly created user and computer objects. Set the DN as the OU you want the objects to be created in.Redircmp "CN=Computers,OU=BHP,DC=company,DC=com"
Redirusr "CN=Users,OU=BHP,DC=company,DC=com"
nslookup debugging
To debug / troubleshoot with nslookup run:nslookup
set debug (or set d2
To run a query against a particular DNS server run the below (eg to query ns1.nickbeare.com for the address associated with google.com):
nslookup google.com ns1.nickbeare.com
Add small pic to website tabs
In the HTML head section add the below:link rel="shortcut icon" href="img/portfolio/icon.png"/>
How to use a wireless adapater on Windows Server 2012 R2
Add the Wireless LAN Service feature using server manager.Start the WLAN AutoConfig service in services.msc.
Adding bulk DNS records with dnscmd
The below command can be run from the command line on a DNS server that is authoritative for the intended zone. This command will create multiple A records, but it does not create the associated pointer record.for /f "tokens=1-3" %i in (forward.txt) do dnscmd %COMPUTERNAME% /RecordAdd %k %i A %j
forward.txt will contain the A records you want to add in the format of hostname, IP address, zone.
Sample file:
host1 192.168.1.115 test.local
host2 192.168.1.116 test.local
host3 192.168.1.117 test.local
To create the pointer records run the below command:
for /f "tokens=1-3" %i in (reverse.txt) do dnscmd %COMPUTERNAME% /RecordAdd %k %i PTR %j
reverse.txt will contain the PTR records you want to add in the format of octet, FQDN, reverse lookup zone.
Sample file:
115 host1.test.local 1.168.192.in-addr.arpa
116 host2.test.local 1.168.192.in-addr.arpa
117 host3.test.local 1.168.192.in-addr.arpa
A more effective way to perform the bulk add is to use batch to add the PTR and A records in a single script. Note, the variable sign in batch is %%, the pause flag ensures that you can double click on the .bat file without the output disappearing.
for /f "tokens=1-4" %%i in (c:\users\administrator\desktop\entries.txt) do dnscmd %COMPUTERNAME% /RecordAdd %%k %%i %%l %%j
@ pause
The single sample file for forward and reverse entries:
beare1 192.168.1.140 lucas.com A
beare2 192.168.1.141 lucas.com A
beare3 192.168.1.142 lucas.com A
140 beare1.lucas.com 1.168.192.in-addr.arpa PTR
141 beare2.lucas.com 1.168.192.in-addr.arpa PTR
142 beare3.lucas.com 1.168.192.in-addr.arpa PTR
Service Principal Name (SPN)
A service principal name (SPN) is the name by which a client uniquely identifies an instance of a service.
List registered SPNs on a host/user:
setspn -L hostname/username
Create an SPN:
Syntax: setspn serviceclass/host:portnumber servicename
setspn -A HTTP/myappserver.austin.ibm.com myappserver
Delete an SPN:
setspn -d mssqlsvc/sql_hostname.test.org:1400 svc_serviceaccountname
Searching for duplicate SPNs. On a 2008 server run:
setspn -x
Hide tabs/settings from Internet Options in Internet Explorer
To restrict all user accounts, create the keys under HKEY_LOCAL_MACHINE instead of HKEY_CURRENT_USER.
Under the below key:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\
Create a new key "Control Panel" under the "Internet Explorer" key.
Accessibility - Disables options in "Accessibility" window in "General" tab
Advanced - Disables options in "Advanced" tab
AdvancedTab - Completely hides "Advanced" tab
Autoconfig - Disables "Automatic Configuration" section in "LAN Settings" window under "Connections" tab
Cache - Restricts changes to Temporary Internet Files settings
CalendarContact - Restricts changes to Calender and Contact List options
Certificates - Restricts changes to Security Certificates in "Content" tab
CertifPers - Restricts changes to Personal Certificates in "Content" tab
CertifPub - Restricts changes to Publisher Certificates in "Content" tab
CertifSite - Restricts changes to Site Certificates in "Content" tab
Check_If_Default - Restricts checking IE as default browser in "Programs" tab
Colors - Restricts changes to "Colors" window in "General" tab
Connection Settings - Disables options in "Connections" tab
Connection Wizard - Disables Internet Connection Wizard
ConnectionsTab - Completely hides "Connections" tab
Connwiz Admin Lock - Disables "Setup Internet Connection" button in "Connections" tab
ContentTab - Completely hides "Content" tab
Fonts - Disables options in "Fonts" window in "General" tab
FormSuggest - Disables AutoComplete Settings for Forms in "Content" tab
FormSuggest Passwords - Disables AutoComplete Settings for Passwords in "Content" tab
GeneralTab - Completely hides "General" tab
History - Restricts changes to History settings in "General" tab
HomePage - Restricts changes to Home page settings in "General" tab
Languages - Restricts changes to "Languages" window in "General" tab
Links - Restricts changes to Links settings in "General" tab
Messaging - Restricts changes to E-mail, Newsgroups, Internet call options in "Programs" tab
Privacy Settings - Restricts changs to Cookies settings in "Privacy" tab
PrivacyTab - Completely hides "Privacy" tab
Profiles - Restricts changes to Profiles in "Content" tab
ProgramsTab - Completely hides "Programs" tab
Proxy - Disables "Proxy server" section in "LAN Settings" window under "Connections" tab
Ratings - Restricts changes to "Content Advisor" settings in "Content" tab
ResetWebSettings - Disables "Reset Web Settings" button in "Programs" tab
SecAddSites - Disables "Sites" button in "Security" tab
SecChangeSettings - Restricts changes to Security Level in "Security" tab
SecurityTab - Completely hides "Security" tab
Settings - Restricts changes to Temporary Internet Files options
For example, if you want to hide the "Advanced" tab, create new DWORD value AdvancedTab and set its value to 1. To remove the restriction, either change the DWORD value to 0 or delete the DWORD value.
If you want to disable the whole "Internet Options" window from the Tools menu, go to following key:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\
Create a new key "Restrictions" under the "Internet Explorer" key. In right-side pane, create a new DWORD value NoBrowserOptions and set its value to 1.
Determine the NTP source on XP & Server 2003
The equivalent of w32tm /query on XP and 2003 is "net time /querysntp".Export a DNS zone to a text file
dnscmd /zoneexport bhp.com.au output.txtThe output file will be found in c:\windows\system32\dns.
Run Windows Explorer as a different user
runas /user:administrator "explorer.exe /separate"Bulk add groups in AD
-scope g - Global group-scope L - Domain Local group (Could also be -scope l. Lower case L)
-secgrp yes - Security group (not distribution)
dsadd group "cn=ICT, ou=corporate, dc=bhp, dc=com" -secgrp yes -scope L -desc "Object Description"
Some useful dnscmd commands
Show all zones that a DNS server is authoritative for:DnsCmd ServerName /EnumZones
Reload an entire zone from file or from the primary nameserver:
DnsCmd ServerName /ZoneReload ZoneName
Commence incremental zone transfer from primary name server:
DnsCmd ServerName /ZoneRefresh ZoneName
Windows netstat - finding connected sessions by port number
Eg to find connected ftp client sessions on your server:netstat -np TCP | find ":21"
Viewing Nework Configuration with WMI
Get-WmiObject -Class Win32_NetworkAdapter -ComputerName host1View all shares on a server/workstation
net view hostnameFind uptime on a windows box using cmd
The information is also listed in task manager under the performance tab.systeminfo | find /i "system boot time"
Demoting a DC in 2012
Remove the AD DS role using server manager and select depromotePre-staging computers
Pre-staging is creating a computer object in AD in an OU or container before the computer has been added to the domain. When the computer is added to the domain it is automatically mapped with the pre-staged computer object in that particular OU or container.
Trusted Sites
You can use Group Policy to create trusted sites.See Computer Configuration --- Administrative Tools --- Windows Components --- Internet Explorer --- Internet Control Panel --- Security Page and then double click to the "Site to zone assignment list".
Enable it, click Show, add website as value name and 1, 2, 3 or 4 as value.
1. Intranet zone
2. Trusted Sites zone
3. Internet zone
4. Restricted Sites zone
Website examples:
*.bhp.com.au
hostname
www.whoknows.com
HP ProLiant MicroServer - How to Enable SATA RAID and Create Logical Disk
LinkHow to join two cells together in Excel and separate then with a '.' (or any other character).
=""&A1&"."&B1&""Exporting site/subnet info
You can use dssite.msc and export the list of sites and their associated subnets as a csv file (right click export).
You can also use dsquery:
dsquery subnet | dsget subnet -site -dn
OR
dsquery subnet -site some_site_name
Terminal Services Administrator snapin
tsadmin.mscDHCP server logs
DHCP server logs do not appear in the Event Viewer. They need to be enabled on the DHCP server. In dhcpmgmt.msc right click on the server, select properties, tick Enable DHCP Audit Logging. The logs are recorded in c:\WINDOWS\system32\dhcp in comma deliminated text files, one file per day.Reset password from command line
net user username * /domainShow all authorised DHCP servers
netsh dhcp show serverSetting up RDP licences
Add the remote desktop session host role.Computer Configuration - Administrative Templates - Windows Components - Remote Desktop Session Host - Licensing
Use the specified remote desktop licence servers - enter licence server here.
Set the remote desktop licencing mode - user or computer.
How to turn on/off IE ESC mode via the registry
This change can be made via group policy using group policy preferences (registry).HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}
IEHardenAdmin
Value of IsInstalled should be 0, if disabling for Administrators and 1, if enabled.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073}
IEHardenUser
Value of IsInstalled should be 0, if disabling for users and 1, if enabled.
Group Policy location for adding DNS Search Suffix Lists
Computer Configuration\Administrative Templates\Network\DNS Client\DNS Suffix Search List.Creating a keytab file
You can use a keytab file to authenticate to various remote systems using Kerberos without entering a password. However, when you change your Kerberos password, you will need to recreate all your keytabs.Keytab files are commonly used to allow scripts to automatically authenticate using Kerberos, without requiring human interaction or access to a password stored in a plain-text file. The script is then able to use the acquired credentials to access files stored on a remote system. Generation of the keytab file also registers the relevant SPNs against the account name (visible via setspn -L account_name). Note you can only have one SPN registered per service.
Keytab files can also be used to allow a third party to authenticate users from your domain.
Further reading here
Sample code to create a keytab file and associate it with the HTTP service below. Be careful, the password switch will reset the account's password if you enter a different password to the account's current password, consequently invalidating any previously issued keytab files.
ktpass -out C:\temp\file.keytab -princ HTTP/hostname@BHP.COM -pass insert_password -mapuser BHP\insert_account -ptype KRB5_NT_PRINCIPAL -crypto RC4-HMAC-NT -kvno 1
Group Policy setting to end Disconnected sessions (other than console ones)
Computer Configuration/Policies/Administrative Templates/Windows Components/Remote Desktop Services/Remote Desktop Session Host/Session Time LimitsSet time limit for disconnected sessions
How to log on as Local System
Psexec will allow you to become the local system account. Just use the -s flag eg psexec.exe -s cmd.exe.How to start a packet capture with netsh
To start it:netsh trace start persistent=yes capture=yes tracefile=c:\temp\nettrace.etl
To end the capture:
netsh trace stop
You can then use Windows Network Monitor to open the capture file (.etl). Make sure in Network Monitor you go to Tools - Options - Parser Profiles - Windows, then hit Set As Active and click OK. This make the capture more readable.
Further reading
Allow the storing of passwords and credentials in scheduled tasks
A Computer Configuration setting.In Group Policy Editor go to:
Windows Settings
Security Settings
Local Policies
Security Options
Network access: Do not allow storage of passwords and credentials for network authentication - "Set this setting to disabled"
Network Level Authentication
Network Level Authentication is a technology used in Remote Desktop Services (RDP Server) or Remote Desktop Connection (RDP Client) that requires the connecting user to authenticate themselves before a session is established with the server.You can disable/enable this requirement of the client on a server by applying the "Require user authentication for remote connections by using Network Level Authentication" Group Policy setting.
This Group Policy setting is located in Computer Configuration, Policies, Administrative Templates, Windows Components, Remote Desktop Services, Remote Desktop Session Host, Security.
Show which server has permission to scavenge a DNS zone
Run:dnscmd /zoneinfo bhp.com
At the bottom of the output the IP address of the server which has the permission to scavenge the zone is shown.
To change the scavenging server for a zone, run the command:
dnscmd /zoneresetscavengeservers bhp.com "IP of the current DNS Server"
GPO WMI Filter
The below GPO WMI Filter can be used to target 2008 and 2008R2 servers. The versioning numbers refer to the OS and a product type of 3 is for a server, 1 should be for a desktop OS.SELECT * FROM Win32_OperatingSystem WHERE (Version like "6.1%" OR Version like "6.0%") AND ProductType="3"
How to install SSH server on Windows
LinkSynchronising two directories using WinSCP (like rsync)
Place both files in C:\Program Files (x86)\WinSCP
Create a bat file with the below:
winscp.exe /console /script=transmission.txt /timeout=600
Your script file below in txt format:
open saved_session_name
synchronize local E:\source /home/remote_user/Downloads -resumesupport=on
Custom ADM to configure auto-logon on workstations
VALUE makes a REG_SZ record (string) and VALUE NUMERIC makes a REG_DWORD (number). Once you enable the setting the registry entries in the action list are applied. The AutoLogonCount is required to ensure that the account doesn't automatically login after a logoff. The AutoAdminLogon being set to 1 enables autologon (0 turns it off). The KIOSK entry is just a unique identifier (tattoo) for informational purposes.
CLASS MACHINE
CATEGORY "KIOSK"
KEYNAME "SOFTWARE\Microsoft\Windows NT\CurrentVersion\winlogon"
POLICY "KIOSK AUTO LOGON"
VALUENAME "KIOSK"
VALUEON NUMERIC 1
ACTIONLISTON
VALUENAME "DefaultPassword" VALUE "enter_password"
VALUENAME "DefaultDomainName" VALUE "enter_domain"
VALUENAME "DefaultUserName" VALUE "enter_accountname"
VALUENAME "AutoAdminLogon" VALUE "1"
VALUENAME "AutoLogonCount" VALUE NUMERIC 1
END ACTIONLISTON
END POLICY
END CATEGORY
How to set up WSUS
In 2012 R2 it is very simple to set up a WSUS server. Basically you add the role, go through the default settings, select the products (eg Windows 10) you want to synchronise your server against, set a synchronisation schedule, and target your clients via group policy. You can configure rules to allow your WSUS server to automatically approve cerain updates. In Depth Guide Here.I noticed that KB3159706 bricked my WSUS service after it was applied on the server (2012R2). WSUS wouldn't start and a SQL error would appear. After removing the patch and rebooting the server, the WSUS service started normally.
Apprently the below manual steps need to be carried out after installing KB3159706:
Open an elevated Command Prompt window, and then run "C:\Program Files\Update Services\Tools\wsusutil.exe postinstall /servicing" (case sensitive, assume C: as the system volume). Select HTTP Activation under .NET Framework 4.5 Features in the Server Manager Add Roles and Features wizard. Restart the WSUS service.
To force a client to check the WSUS server for updates type:
wuauclt /detectnow
To refersh the client's report on WSUS type:
wuauclt /reportnow
The default WSUS port is 8530. 8531 is for SSL.
How to remotely enable RDP
Enable remote desktop, either via regedit or PowerShell. A fDenyTSConnections value of 1 indicates that RDP is not enabled.set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server'-name "fDenyTSConnections" -Value 0
Allow incoming RDP on the Windows firewall:
Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
To enable secure RDP authentication, run the below in PowerShell or make the change using regedit:
set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "UserAuthentication" -Value 1
How to tell what Hyper-V host a VM is running on
You can find the Hyper-V host name in the guest VM’s registry at the following key:HKLM\SOFTWARE\Microsoft\Virtual Machine\Guest\Parameters
Modifying the Windows bootloader using bcdedit
Bcdedit will display the Windows bootloader. Each bootable OS has its own section with the heading encircled in squiggly brackets. To remove an OS from the boot menu type the below, where Windows 10 is used as an example.bcdedit /delete {Windows 10}
DHCP Icons Explained
LinkHow to wipe a disk in Windows when Disk Management won't
Some system/boot partitions are protected from being deleted using Disk Management and other methods. You can still remove these using DISKPART:diskpart
list disk (shows the disks)
select disk x (where x is the number of the disk you want to remove)
list disk (confirmed your selected disk)
clean (wipes the disk entirely, all partitions)
Setting up FTPS in IIS
A great guide for setting up FTPS under IIS is here. A couple of other things to remember:On your FTPS client your login should be in the form of virtual.ftpserver.name|domain\username eg ftp.bhp.com|bhp\nick. You can set the virtual hostname in the FTP sites site bindings section.
Your FTP SSL settings on your server and FTP site may have to match.
Under FTP Authorization rules on your FTP site you can click edit and enter the domain name.
Install a feature using DISM
Useful for installing features if you cannot get out to the web, but have installation media. The below example installs the 3.5 .Net Framework:
DISM /Online /Enable-Feature /FeatureName:NetFx3 /All /LimitAccess /Source:d:\sources\sxs
You can also do things like change the server edition of your OS such as going from Trial to Standard edition. You can also imbed the key:
DISM /online /Set-Edition:serverstandard /ProductKey:xxxx-xxxx-xxxx /AcceptEula
Useful GUI that shows system and hardware specs
msinfo32.exeGetting the PHP mail function working in IIS
I had to add a sendmail_from email address to the mail function and replace localhost in SMTP with my actual mail server name.Executing a command on a remote computer using PSEXEC
Note, this runs the command under the local SYSTEM account.c:\psexec.exe \\computer.domain.com -s \\fileserver\script.bat
How to bypass execution policy when running a powershell script
PowerShell.exe -ExecutionPolicy UnRestricted -File .runme.ps1
How to stop a stuck Windows service
Identify the PID of the stuck service. Open cmd and type:sc queryex. This lists all available services. You may want to direct this output to a text file.
Search the list of services for the problematic service. After you have identified the service on the SERVICE_NAME line note the PID.
Use the taskkill command to kill the process eg for a PID of 1800: taskkill /PID 1800 /F
Re-adding a computer to the domain with only one restart
Substitute computername with the name of the computer you are working with. Update domain and username as required. **** represents typing the password into the cmd prompt for the userd performing the operation. Remove:netdom.exe remove computername /Domain:bhp.com.au /userd:bhp\administrator /passwordd:***************
Join:
netdom.exe join computername /Domain:bhp.com.au /userd:bhp\administrator /passwordd:***************
Listing specific attributes for an AD object such as a user or computer using dsquery
Note -attr * will show all attributes. When querying a computer object put $ at the end of the samaccountname value eg work01$.dsquery * -filter (samaccountname=biz) -attr name whenchanged
Resetting a local Windows account password using Hirens Boot Disk
LinkConnecting to a Remote Desktop license server
A Remote Desktop Session Host (role) server must be able to contact a Remote Desktop license server to request Remote Desktop Services client access licenses (RDS CALs) for users or computing devices that are connecting to the RD Session Host server. You must specify a license server for the RD Session Host server to use. You can do this via group policy. The setting is located in: Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Licensing Enter the licence server name (FQDN). If you don't know the name of the licence server look at which servers are a member of the AD group Terminal Server Licence Servers. Set the type of licence to user or computer. This works cross domain as long as ports are unblocked. Once set, use the MMC RD Licence Diagnoser to verify connectivity to the licence server and that the client is now activated.How to allow RDP when receiving error "no remote desktop license servers available"
Go to the below reg key on the server you are trying to RDP to:HKLM\system\CurrentControlSet\Control\Terminal Server\RCM\GracePeriod
Take ownership, grant yourself full control, delete the REG_BINARY value contained within GracePeriod, restart the computer.
Monitoring network speeds with iperf
Iperf is a tool to measure the bandwidth and the quality of a network link.First, on the listening Windows machine type:
iperf -s -i 1 -w 63K
Next, on the sending Windows machine type:
iperf -c servername -r -t 20 -i 1 -w 63K
How to use Cleanmgr without installing the desktop experience
Windows 2008 R2C:\Windows\winsxs\amd64_microsoft-windows-cleanmgr_31bf3856ad364e35_6.1.7600.16385_none_c9392808773cd7da\cleanmgr.exe
C:\Windows\winsxs\amd64_microsoft-windows-cleanmgr.resources_31bf3856ad364e35_6.1.7600.16385_en-us_b9cb6194b257cc63\cleanmgr.exe.mui Windows Server 2012:
C:\Windows\WinSxS\amd64_microsoft-windows-cleanmgr_31bf3856ad364e35_6.2.9200.16384_none_c60dddc5e750072a\cleanmgr.exe
C:\Windows\WinSxS\amd64_microsoft-windows-cleanmgr.resources_31bf3856ad364e35_6.2.9200.16384_en-us_b6a01752226afbb3\cleanmgr.exe.mui Once you’ve located the files move them to the following locations (Server 2012 non-R2 and earlier):
Copy Cleanmgr.exe to %systemroot%\System32.
Copy Cleanmgr.exe.mui to %systemroot%\System32\en-US. Example - open a command prompt and type:
copy C:\Windows\winsxs\amd64_microsoft-windows-cleanmgr_31bf3856ad364e35_6.1.7600.16385_none_c9392808773cd7da\cleanmgr.exe C:\windows\system32
copy C:\Windows\WinSxS\amd64_microsoft-windows-cleanmgr.resources_31bf3856ad364e35_6.2.9200.16384_en-us_b6a01752226afbb3\cleanmgr.exe.mui C:\windows\system32\en-US You can now launch the Disk cleanup tool by running Cleanmgr.exe from the command prompt.
Troubleshooting failed SCCM builds
Once the boot image is loaded and the OS is starting up press F8 to bring up a command prompt. If the task sequence errors the machine will not reboot as long as the command prompt is up. From the command prompt you can view the smsts.log which logs the build process. This gets written to the C drive once the C drive is created by the task sequence. If your task sequence errors out before C drive can be created then smsts.log will be stored in memory under X:\SMSTS\smsts.log.Another way to determine uptime on a server or workstation
net statistics servernet statistics workstation
Robocopy command to copy directory and child folders and files to another location
robocopy "\\source\source" "\\destination\destination" /E /ETA/E :: copy subdirectories, including Empty ones
/ETA :: show Estimated Time of Arrival of copied files.
SMSTS.log file locations during OS deployment
Before your hard drive is formatted and partitioned:X:\windows\temp\smstslog\ After your hard drive is partitioned formatted:
X:\smstslog\ and then is in C:\_SMSTaskSequence\logs\smstslog\ Within Windows before the SCCM agent is installed:
C:\_SMSTaskSequence\logs\smstslog\ Within Windows after the SCCM agent installed:
C:\windows\system32\ccm\logs\smstslog\ When the Task Sequence completes on a x86:
C:\windows\system32\ccm\logs\ For x64 Systems:
C:\windows\SysWOW64\ccm\logs\
How to track disk utilisation using perfmon
You can use perfmon.msc to create a data collector set using the below counters to accurately measure disk utilisation.
Source
Creating a Striped Volume using DiskPart
First wipe both disks, convert them to GPT, and set them to dynamic:select disk 0 clean convert gpt select disk 0 convert dynamicCreate the striped volume across both disks, using all available space:
create volume stripe disk=0,1Format and assign a drive letter to the new volume:
format fs=ntfs quick assign How to manually delete left over windows updates files
Useful for when you're trying to clean up disk space. Clear out the C:\Windows\softwareDistribution\Download\ directory.How to remove GRUB bootloader and use Windows
From command prompt:bootsect /nt60 c: /mbr