Active Directory Tips
How to reset the Directory Services Restore Mode (DSRM) password
Using ntdsutil to reset the DSRM password:
Compacting/Defragging NTDS.dit
First, take AD DS offline by stopping the 'Active Directory Domain Services' service. When prompted stop the associated child services. Run the below ntdsutil commands in an administrative command prompt:Copy the newly compacted ntds.dit file over the original ntds.dit file using windows explorer. Note, the default location for ntds.dit is c:\Windows\NTDS\. Finally, restart the 'Active Directory Domain Services' service.
Moving (cut) the NTDS database and log files
First, take AD DS offline by stopping the 'Active Directory Domain Services' service. When prompted stop the associated child services. Run the below ntdsutil commands in an administrative command prompt. The info command shows the current location of the NTDS files.Finally, restart the 'Active Directory Domain Services' service.
Authoritative and Non-Authoritative Restores
In order to perform either restore you will first need a backup of the DC that includes the system state.
Backup the system state with wbadmin. In this example it is backed up to the local E
drive:
wbadmin start systemstatebackup -backupTarget:e:
Next restart the DC into DSRM. Run the below command to get information about your
current backup:
wbadmin get versions -backuptarget:e: -machine:hostname
Restore the system state using your backup (don't reboot at the end unless you are doing a non-authoritative restore):
wbadmin start systemstaterecovery -version:04/30/2013-09:00 -backupTarget:\\localhost\e$ -machine:hostname
If you are performing a non-authoritative restore then the process is complete after a reboot. The other DCs will replicate changes to AD since the last system state backup.
To perform an authoritative restore to restore for example the BHP OU and all of its
child objects:
ntdsutil
activate instance ntds
authoritative restore
restore subtree "OU=bhp,DC=nuggetlab,DC=com"
q
q
Restart the server in normal mode.
Authoritative Restore Demonstration
Check the schema version as well as other information
Open regedit and navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NTDS\Parameters:Decimal value meanings:
Windows 2000 RTM with all Service packs = Schema version 13
Windows Server 2003 RTM with all Service packs = Schema version 30
Windows Server 2003 R2 RTM with all Service packs = Schema version 31
Windows Server 2008 RTM with all Service packs = Schema version 44
Windows Server 2008 R2 RTM with all Service packs = Schema version 47
Windows Server 2012 RTM = Schema version 56
Dcpromo unattended install command
dcpromo /unattend:c:\temp\unattendfile.txt
Sample unattend file:
Breakdown of the structure of a SID
Extending the schema with ADPREP
Adprep.exe is a command-line tool that is included on the installation disk of each version of Windows Server. Adprep.exe performs operations that must be completed on the domain controllers that run in an existing Active Directory environment before you can add a domain controller that runs that version of Windows Server.For example, if your organization has domain controllers that run Windows 2000 Server or Windows Server 2003, before you can add a new domain controller that runs Windows Server 2008 R2 or upgrade one of the existing domain controllers to Windows Server 2008 R2, you must run Adprep.exe from the \Support\Adprep folder of the Windows Server 2008 R2 installation DVD on your existing domain controllers.
In Windows Server 2008 R2, Adprep.exe is located in the \Support\Adprep folder of the operating system disk. In Windows Server 2008, Adprep.exe is located in the \Sources\Adprep folder.
To complete the required operations, you must run the Adprep.exe commands that are listed in the following table. You must run adprep /forestprep before you run other commands. Some commands must be run on specific domain controllers, as indicated in the table. None of the commands requires a restart of the server after the operation is complete.
| Command | Domain Controller | Number of times to run the command |
| adprep /forestprep | Must be run on the schema operations master for the forest. | Once for the entire forest. You must be a member of the Schema Admins group, the Enterprise Admins group, and the Domain Admins group of the domain that hosts the schema master. |
| adprep /domainprep /gpprep | Must be run on the infrastructure operations master for the domain. | Once in each domain where you plan to install an additional domain controller that runs a later version of Windows Server than the latest version that is running in the domain. Requires Domain Admin credentials. |
| adprep /rodcprep | Can be run from any computer. If you already ran this command for Windows Server 2008, you do not have to run it again for later versions of Windows Server. | Once for the entire forest. Requires Enterprise Admin credentials. |
Note, beginning with Windows Server 2012, Adprep.exe is integrated into the AD DS installation process and runs automatically as needed. For example, when you install the first domain controller that runs Windows Server 2012 into an existing domain and forest, then adprep /forestprep and adprep /domainprep automatically run and report the results of the operations.
FSMO roles
Domain specific rolesPDC Emulator:
* Provides legacy support for Windows NT 4.0 BDCs.
* Is the time synchronization source for all other domain controllers. In a multi-domain forest the PDC Emulator in each domain synchronizes to the forest root PDC Emulator.
* All password changes occur on the PDC Emulator and receive priority replication.
RID Master:
Responsible for processing RID Pool requests from all DCs within the domain. The RID Master responds to these requests by retrieving RIDs from the domain's unallocated RID pool and assigning them to the pool of the requesting DC (approx 500 RIDs). The requesting DC then uses these RID when creating security principal objects such as a users or groups.
Infrastructure Master:
Ensures that cross-domain object references are correctly handled. For example, if you add a user from one domain to a security group from a different domain, the Infrastructure Master makes sure this is done properly. if your Active Directory deployment has only a single domain, then the Infrastructure Master role does no work at all.
Forest specific roles
Schema Master:
The purpose of this role is to replicate schema changes to all other domain controllers in the forest. The schema is the blueprint of Active Directory and defines what kinds of objects can exist in the Active Directory database and the attributes of those objects.
Domain Naming Master:
Processes all changes to the namespace, for example adding the child domain vancouver.mycompany.com to the forest root domain mycompany.com requires that this role be available.
LSDOU
LSDOU is a group policy inheritance model (scope of management), where policies are applied in the order of Local machines, Sites, Domains and Organizational Units.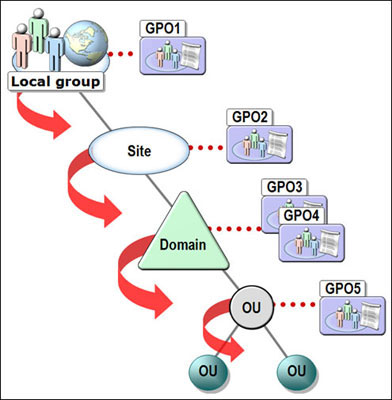
FFL and DFL features
2003 Domain Functional Level (DFL) - requires at least Windows Server 2003 DCs in the domain.* Can now rename DCs
* Additional Object Class: inetorgperson (account migrated from non-AD OS, works like a normal user account)
* Additional Attributes: lastlogontimestamp, user password (relates to inetorgperson)
* redirusr and redircmp: sets a default OU to house created user or computer objects.
* Selective Authentication: Used in forest trusts to discriminate what accounts can be authorised over the forest trust and what recsources they can access.
* Constrained Delegation: allows a computer or user account to manage services on another computer.
* Authorisation Manager: Allows application developers to create applications in which only particular users can access certain features of the application.
2008 Domain Functional Level (DFL) - requires at least Windows Server 2008 DCs in
the domain.
* DFS-R SYSVOL replication: More efficient bandwidth utilisation than FRS.
* Additional Attributes: Last Logon (number of failed logon attempts since last log on,
workstation they attempted to log onto).
* Fine-Grained Passwords: Previously in a 2003 DFL you could only have one domain
password policy (GPO) for the entire domain. Now in 2008 DFL we can have multiple
Fine-Grained password policies linked to security groups and users.
* Advanced Encryption Services (AES) 128/256 bit encryption for kerberos
authentication. Old version of Kerberos in 2003 DFL was RC4HMAC (secure).
2003 Forest Functional Level (FFL) - requires at least Windows Server 2003 DCs in
all domains in the forest.
* Forest Trusts: allows two separate forests to share resources as if they were in the
same forest.
* Can now rename Domains
* Linked Value Replication - replicates only new content eg a user is added to a group
which already has 50 users. LVR replicates only the single user, not the entire
group membership.
* RODC: contains a read-only copy of AD, doesn't have passwords stored on it (unless
you cache them for particular users). PDC Emulator role must be on a 2008 DC. The
RODC must receive AD replication updates from a 2008 DC. Only one RODC per domain,
per site is allowed. Cannot have 2 RODCs for the same domain in the same site.
* Improved KCC algorithms for intersite replication (ITSG, calculates the most
efficient path between sites for replication)
* inetorgperson/user conversion
* Deactivate/redefine schema object classes and attributes
2008 Forest Functional Level (FFL) - requires at least Windows Server 2003 DCs in
all domains in the forest.
No new features over 2003 FFL
2008 R2 - Active Directory Recycle Bin
To enable the Recycle Bin, you must be at the Server 2008 R2 forest and domain functional levels.
Restoring deleted objects using tombstone reanimation
When Active Directory deletes an object from the directory, it does not physically remove the object from the database. Instead, Active Directory marks the object as deleted by setting the object’s isDeleted attribute to TRUE, stripping most of the attributes from the object, renaming the object, and then moving the object to a special container in the object’s naming context (NC) named CN=Deleted Objects. The object, now called a tombstone, is invisible to normal directory operations.The default tombstone lifetime is 60 days for forests initially built using Windows® 2000 and Windows Server 2003, and 180 days for forests that were initially built with Windows Server 2003 SP1. You can change the tombstone lifetime by using ADSIEdit to modify the tombstoneLifetime attribute of the CN=Directory Service,CN=Windows NT, CN=Services,CN=Configuration, DC= object.
The Deleted Objects container is hidden and cannot be viewed by using Active Directory Users and Computers and ADSIEDIT.MSC. But you can use LDP.EXE.
* Open LDP
* Go to Connection – Bind – ‘Bind as currently logged on user’
* Go to Options – Controls. On Load Predefined, select 'Return deleted objects' click OK.
* Go to View – Tree – Enter the baseDN for your domain eg DC=Nuggetlab,DC=com
Then expand the Deleted Objects container, and find the user you deleted and click modify.
* In the Attribute box, type isDeleted. Under Operation, click Delete, and then click Enter.
* In the Attribute box, type distinguishedName, in the Values box, type the DN eg CN=Jenny,OU=Marketing,DC=nuggetlab,DC=com. Under operation, click Replace, and then click Enter.
* Select the Extended check box, and then click Run.
You can now view the reanimated object in AD Users and Computers. Note, the result of restoring deleted objects using the Tombstone Reanimation procedure is not perfect. For example if you restore a user object it will be disabled and stripped of all attributes.
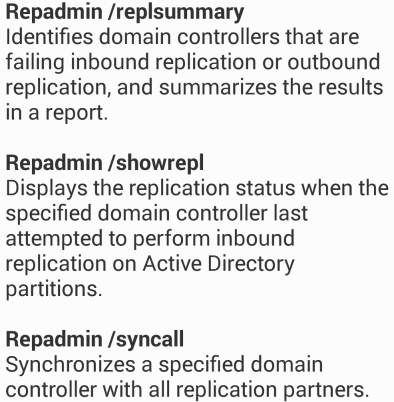
Using repadmin to check replication health
To check the replication status of all Domain Controllers in the forest type:repadmin /replsummary *
This command provides a general outline of replication health throughout the forest. The ‘%% error’ and ‘Fails’ columns record replication link failures. The ‘total’ column represents the total number of replication links for a DC (one for each naming context, this does not represent replication partners). The ‘largest delta’ is the longest replication amongst all replications links (total column) for a DC.
In the below screenshot we can see that replication issues are occurring.
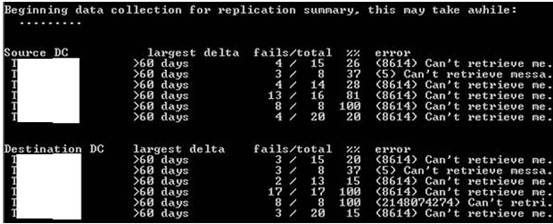
If the above command reports any replication problems, the below command can be run on an individual DC that is reporting replication failures (remember to enter the relevant DC name).
repadmin /replsummary insert_DC_name_here
The results of this command allow us to narrow down where the replication issue is coming from. In the below screenshot we can see that the last Source DC is causing the problem.

Now that the problematic DC has been identified, the below command should be run to return more detailed information about the replication problem. Note, you will need to replace c:\file.csv with the relevant path and desired filename:
repadmin /showrepl insert_DC_name_here /csv > “c:\file.csv”
In the below screenshot you can see in the ‘Last Success Time’ column that replication has failed since 14/08/2014. You can also see the ‘Last Failure Time’. The Naming Context’ column indicates which AD partitions the DC has having issues replicating. The next step is to resolve the replication problem by further investigating the error, in this case 8614, in the ‘Last Failure’ column.
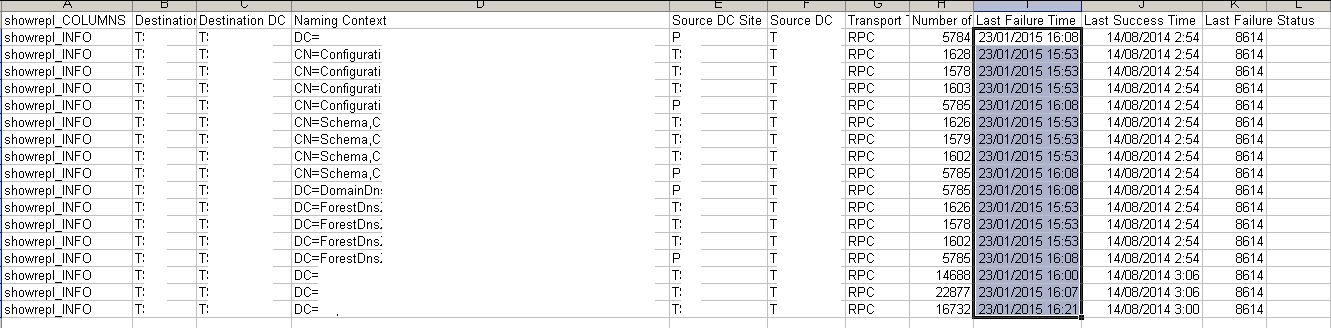
Running a DC health check
dcdiag /s:dc_hostname /v /c > c:\temp\dc_health_check.txtIf you want to check all DCs in the site use /a instead of /s. If you want to check all DCs in the enterprise use /e. /c runs a comprehensive set of tests.
How to perform a metadata cleanup of a DC
Clean up metadata:i) Open a command prompt and type: Ntdsutil
ii) At the ntdsutils> prompt, type: metadata cleanup
2) Select target server:
i) At the metadata cleanup> prompt, type: connections
ii) At the connections> prompt, type: connect to server PDCE
iii) Ensure binding was successful.
iv) At the connections> prompt, type: quit
3) Select domain::
i) At the metadata cleanup> prompt, type: select operation target
ii) At the select operation target> prompt, type: list domains
iii) A numbered list of domains will be displayed:
Type: select the appropriate domain eg select domain 1 (1 - DC=bhp,DC=gov,DC=au)
4) Select site:
5) Finish Metadata Cleanup:
6) Follow-up Checks:
certutil –dspublish –f “cert_name.cer” RootCA
If using Windows Server 2008 R2 it is much simplified by using the Active Directory Modules for Powershell. Just open a Powershell prompt and use the following command line to verify the location:
1. Open the Active Directory Users and Computers snap-in.
7. Select Only the following objects in the folder, check Computer objects, check the Create selected objects in this folder box, and press Next.
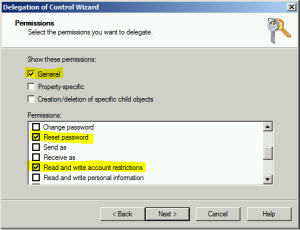
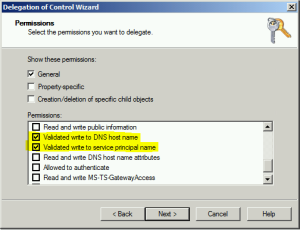
8. Check Reset Password, Read and write account restrictions, Validated write to DNS host name, Validated write to service principal name. Click Next and Finish.
9. Press Finish.
The default value of the TSL depends on the version of the operating system that is running on the first domain controller that is installed in a forest. The following table indicates the default TSL values for different Windows operating systems.
Using Repadmin to remove lingering objects ServerName = The name of the domain controller that has lingering objects, as identified in the event message (event ID 1388 or event ID 1988). You can use the Domain Name System (DNS) name or the distinguished name. ServerGUID = The GUID of a domain controller that has an up-to-date writeable replica of the directory partition that contains the lingering object. DirectoryPartition = The distinguished name of the directory partition that is identified in the event message. For example, DC=RegionalDomainName,DC=ForestRootDomainName,DC=com for a domain directory partition, CN=configuration,DC=ForestRootDomainName,DC=com for the configuration directory partition, or CN=schema,CN=configuration,DC=ForestRootDomainName,DC=com for the schema directory partition
Example:
CLASS USER
[strings]
policyName="Check for publisher's certificate revocation"
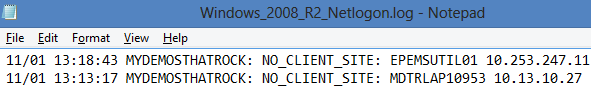
review the netlogon.log to find IP addresses or machines which are not linked to any subnet / site in Active Directory. These entries are listed as NO_CLIENT_SITE in the NETLOGON.LOG file on the authenticating DC (C:\Windows\Debug).
Review the File Replication Service event logs
1.Log on to the effected Domain Controller using an administrator account.
Perform a nonauthoritative mode restore of the SYSVOL
5.Open Services and locate the ‘File Replication Service’
7.Open Regedit. i.e. Start - Run - Regedit
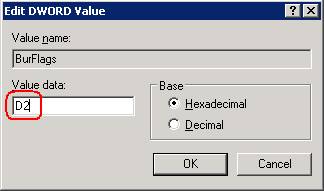
10.Change the ‘Valve Data’ field to ‘D2’ and click OK.
11.Return to Services and Start the ‘File Replication Service’
Confirm SYSVOL replication completion
13.Allow time for the SYSVOL to replicate. This will vary depending on the current size of the SYSVOL folder and the link speed between the DC’s
$userlist=import-csv C:\temp\users.csv
import-module -name activedirectory
Input file sample:
To determine the tombstone lifetime for the forest using ADSIEdit:
Click Start, point to Administrative Tools, and then click ADSI Edit.
Group Policy can be use to terminate Disconnected RDP sessions. Computer Configuration - Administrative Templates - Terminal Services - Sessions.
You can also set these timeouts on the AD user account in ADUC (Sessions tab).
In the Registry Editor, navigate to HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
The DC will then publish the priority of its LDAP and Kerberos SRV records to the DNS zone.
nltest /server:computername_to_test /sc_query:domain.com
nltest /server:computername_to_test /sc_verify:domain.com
Shows particular attribute values for a nominated DC.
Right click on Default Naming Context and select New - Query.
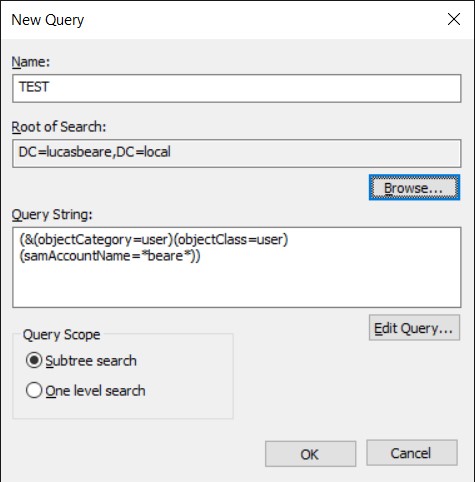
You can use the GUI to generate your Query or type it in manually. Make sure you name your query and select the root of your search. If you want your search depth to be within the OU select One level search. Below is a command that can be used to find any user that has beare in their username.
Your query will now be listed under the Default naming context. Right click on a returned object and select Properties. You can then modify/view all the object’s attributes.
To search for a group use:
Permissions Tab
Permissions Tab
Properties Tab
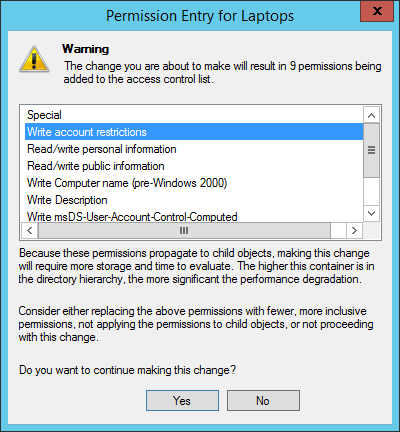
At the end you just have to confirm the change of permissions:
If you want to delegate only move permissions, apply only these settings which are underlined above. Remember that it has to be done on both –source and destination OU.
Microsoft recommends the network adapter DNS to be configured with the address of another DC first, and the local IP second. Otherwise at bootup you risk delaying service startup since if it first hits the local host and the local DNS server service isn't yet operational, it will hang for a while. If the other DC is queried first (and there MUST be another one available, otherwise your network architecture and boot procedures aren't correct), there will be no hang.
To Reset the DSRM Administrator Password Click, Start, click Run, type ntdsutil, and then click OK.
-or-
for /f "Tokens=1-4 Delims=/ " %%i in ('date /t') do set DT=%%i-%%j-%%k-%%l
The default value is 25 in Server 2008.
This value determines how often a domain member will attempt to change its computer account password. The default value is 30 days.
Select the "Authenticated Users" security group and then scroll down to the "Apply Group Policy" permission and un-tick the "Allow" security setting. Note: That the "Allow" permission for "Read" still needs to remain ticked.
Click on the "Add" button and select the group that you want to have this policy apply. Then select the group (e.g. "Accounting Users") and scroll the permission list down to the "Apply group policy" option and then tick the "Allow" permission.
The permissions applied to users belonging to protected groups are more stringent than the default permissions applied onto other user accounts. The default behaviour is that inheritance is disabled on these privileged accounts, ensuring that permissions applied at the parent level aren't inherited by the protected objects, regardless of which OU they reside.
Next Enable auditing on the DNS zone. Open adsiedit.msc on a DC. Connect to the partition the DNS zone is stored ie DC=DomainDNSZones,DC=contoso,DC=com. Under CN=MicrosoftDNS you will find DC=your zone name (ie DC=contoso.com). Right click on that and select Properties. On the Security tab, click the Advanced button. Select the Auditing tab, and click Add. Under User or Group, type ‘Everyone’ and click on Check Names button. Click OK. On the Auditing Entry window that pops up, under the Object tab, select Success and Failure for access types Write All Properties, Delete, and Delete Subtree and click Ok.
After you have set up auditing by following the above mentioned steps, an Event ID (566 in Windows Server 2003 and 4662 in Windows Server 2008 R2) will be logged in the Security Event Log whenever a DNS record is modified.
Run the command:
Make sure that you create the backup volume on a dedicated internal or external hard drive. A network shared folder cannot be used as a backup target for a system state backup. If you want to store a system state backup on a network shared folder, you would have to initially backup to a local volume and then copy the backup to the network shared folder.
$dcs = dsquery server -o rdn
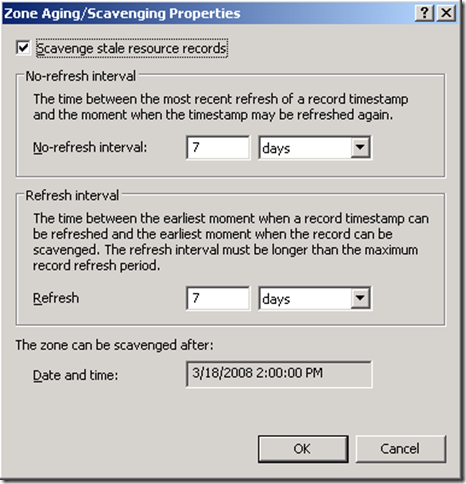
The no-refresh interval specifies how long a client cannot dynamically update their associated DNS record for. The aim of this interval is to reduce replication. Once the no-refresh interval has passed (DNS record timestamp + no-refresh interval), the record enters the refresh interval.
The refresh interval specifies how long a client has to update the timestamp on their associated DNS record. If a client does not update the timestamp on their associated DNS record within the refresh interval, the record becomes illegible for scavenging. The next time scavenging runs on the DNS server (scavenging period) the record will be removed.
DNS zone refresh intervals:
DNS server scavenging interval:
Use w32tm to convert to human readable date:
See the below link on how to demote a 2012 DC using the GUI.
The below example seizes all 5 FSMO roles.
i) At the select operation target> prompt, type: list sites
ii) A numbered list of sites will be displayed. Type: select site
iii) At the select operation target> prompt, type: list servers in site
iv) A numbered list of all servers in that site will be displayed. Type: select server
Where number refers to the DC to be removed:
Eg: 0 - CN=DC01,CN=Servers,CN=ISA,CN=Sites,CN=Configuration,DC=bhp,DC=gov,DC=au
i) Type:quit
ii) At the metadata cleanup> prompt, type: remove selected server
iii) Click Yes when prompted.
i) Open "AD Sites and Services", expand the appropriate Site, and then delete the specific Server.
ii) Also check that the associated computer object is removed from "AD Users and Computers"
Show last successful replication time with peer DCs
repadmin /showvector /latency "DC=bhp,DC=com,DC=au"
Manually Updating a Secondary DNS Zone
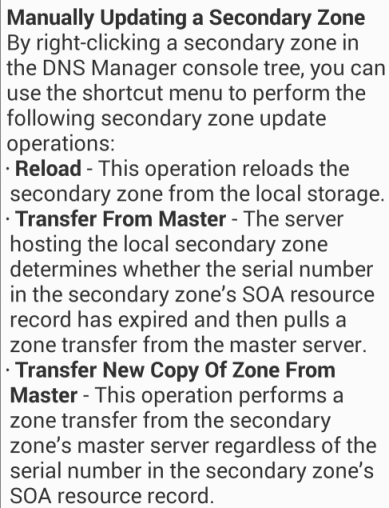
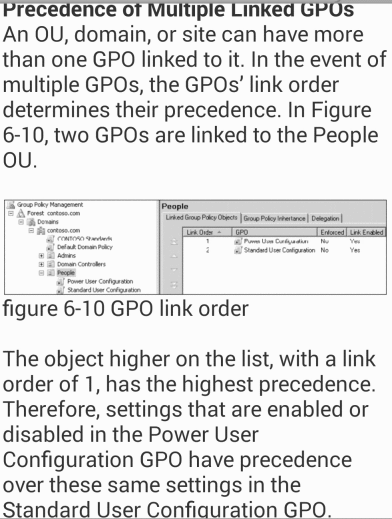
Precedence of Multiple Linked GPOs
Repadmin
Importing and publising certificates
The certutil -dspublish command imports/publishes a certificate to the Root Certificate Authority store in AD, making it available to all domains in the forest. You need to be an Enterprise Admin to publish certs to the Root CA. The -f switch overwrites an existing certificate that has the same name as the one you specify. Once you import a cert using the below command you can verify that the certificate has been published to the Root Certificate Authority store by checking in ADSI Edit: Configuration - Services - Public Key Services - Certification Authorities. Certificates published to this container will be published to the Trusted Root Certification Store on domain joined computers.
Delegate permission to generate Group Policy Results on computers
Link
Verify redirected Computers container in Active Directory
For Windows 2003 and Windows 2008 domains you could verify the actual setting by using either ADSIEDIT (2003) or the ordinary Users and Computers tool (only 2008). Connect to the domain root, select Properties on the domain name and find an attribute called “WellKnownObjects“. The value can be quite long, but look for an entry starting with B:32:AA31. At the end of the hexadecimal numbers you will find the location for new computer accounts.
Get-ADDomain | select computerscont*
Grant a Group rights to join computers to the domain
By default domain users can only add 10 machines to the domain. The below steps outline how to grant permission to a group to join/remove an unlimited number of computers to the domain.
2. Right-click the container under which you want the computers added, and press Delegate Control.
3. Press Next.
4. Press Add.
5. After adding the required group, press Next.
6. Select Create custom task to delegate and press Next.
Removing Lingering Objects from AD
Lingering objects can occur if a domain controller does not replicate for an interval of time that is longer than the tombstone lifetime (TSL). The domain controller then reconnects to the replication topology. Objects that are deleted from the Active Directory directory service when the domain controller is offline can remain on the domain controller as lingering objects.
First domain controller in forest root Default tombstone lifetime
Windows 2000
60 days
Windows Server 2003
60 days
Windows Server 2003 with Service Pack 1
180 days
The syntax of the removal command is:
repadmin /removelingeringobjects ServerName ServerGUID DirectoryPartition /advisory_mode
Repeat step 1 without /advisory_mode to delete the identified lingering objects from the directory partition.
Repeat steps 1 and 2 for every domain controller that might have lingering objects.
Repadmin /removelingeringobjects DC01 a4acc201-5e87-4530-b4d0-f218b16dc0f6 DC=Test,DC=Com
Creating Custom ADM templates
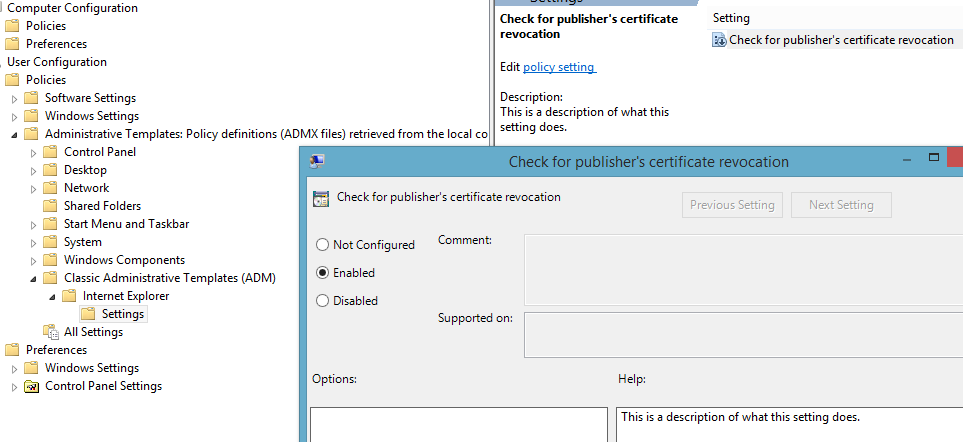
This Guide explains how to create custom ADM files. Below is a sample ADM that changes a single DWORD value in the registry. Download a sample adm.
CATEGORY "Internet Explorer"
CATEGORY "Settings"
KEYNAME "Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing"
POLICY !!policyName
EXPLAIN !!description
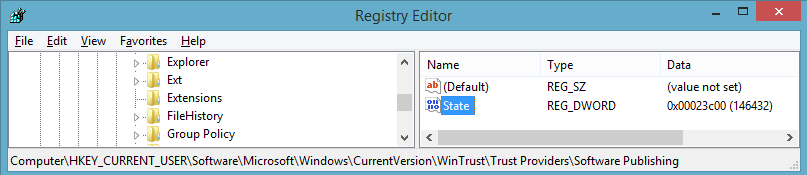
VALUENAME State
VALUEON NUMERIC 146432
VALUEOFF NUMERIC 146944
END POLICY
END CATEGORY
END CATEGORY
description="This is a description of what this setting does."
Find IP addresses or machines which are not linked to any subnet / site
If a computer DOES NOT know the AD site it is in, OR site specific DCs are not responding it will authenticate against a random DC.
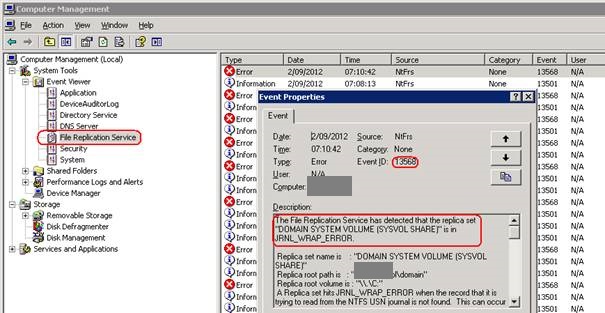
Resolving FRS Journal Wrap mode on a Domain Controller
Network outages and disk problems can cause FRS Journal Wrap on DCs. This results in sysvol not being replicated (inconsistent group policy) and the DC will not be able to fully authenticate users until the journal wrap condition is resolved.
2.Open event viewer
3.Select ‘File Replication Service’
4.Event ID 13568 will be present advising the server is in FRS Journal Wrap
6.Right click on the service name and ‘Stop’ the service
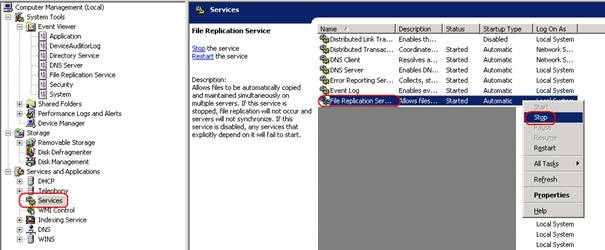
8.Locate the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NtFrs\Parameters\Backup/Restore\Process at Startup
9.Double click the ‘BurFlags’ REG_DWORD
12.Confirm in Event Viewer that ‘File Replication Service’ event ID 13554 is present. This event indicates that the restore of SYSVOL has commenced and the Domain Controllers it will be replicated from.
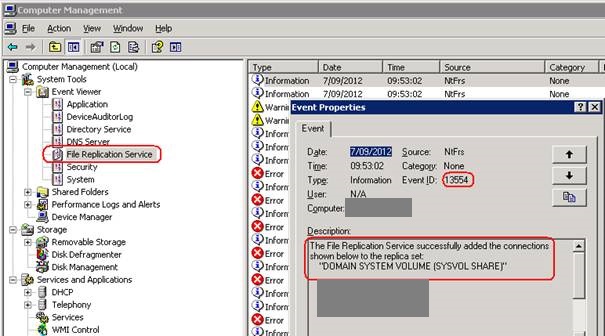
14.Open Event Viewer - File Replication Service.
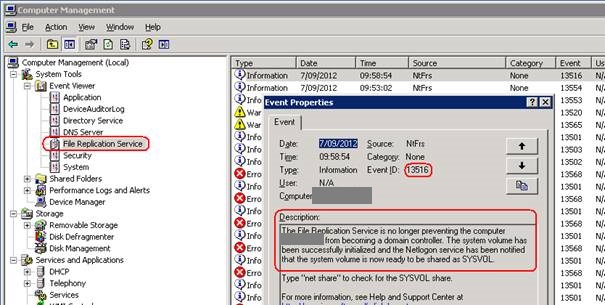
15.Confirm event ID 13516 is present confirming replication of SYSVOL is completed.
Bulk AD User Creation with Excel and DSADD
This spreadsheet can be used to generate DSADD code that can be copied into and run from a batch file to create mass numbers of AD users. You need to fill out the required columns in the Excel spreadsheet and the formulas will fill out the values for DSADD.
Ports required for domain trusts
Open the below ports when creating a domain trust:
88, 389, 445, 636.
Show what site a domain computer thinks it is in
Run this command on the domain computer:
nltest /dsgetsite
PowerShell bulk account creation
Download Excel File
Use the below powershell script with your generated csv file (from the attachment) to create the AD user accounts, make sure you enter a password.
ForEach ($person in $userList)
{
$encryptedpassword=convertto-securestring "Enter_Password" -asplaintext -force
New-aduser -GivenName $person.firstname -name $person.username -Surname $person.surname -DisplayName $displayname -samAccountName $person.username -accountPassword $encryptedpassword -passwordneverexpires $false -changepasswordatlogon $True -path $person.ou -Enabled $True -userprincipalname $person.upn -Description $person.description -verbose
}
PowerShell bulk service account creation
The below PowerShell script can be used to create service accounts.
$accounts = Import-Csv -path "c:\temp\service.csv"
foreach ($account in $accounts)
{
$upn = $account.name + '@BHP.COM.AU'
new-aduser -name $account.name -cannotchangepassword 1 -accountpassword (convertto-securestring -asplaintext $account.password -force) -AccountExpirationDate $null -displayname $account.name -description $account.description -enabled 1 -passwordneverexpires 1 -samaccountname $account.name -userprincipalname $upn -path "OU=Accounts,DC=BHP,DC=COM,DC=AU" -verbose -whatif
}
name,password,description
serviceaccount_name,Password,Sample_Description
Find the Tombstone lifetime for a forest
Tombstone lifetime states how many days a deleted object will remain in the deleted objects container. After the tombstone lifetime is reach the object is completed removed from AD.
In ADSI Edit, right-click ADSI Edit, and then click Connect to.
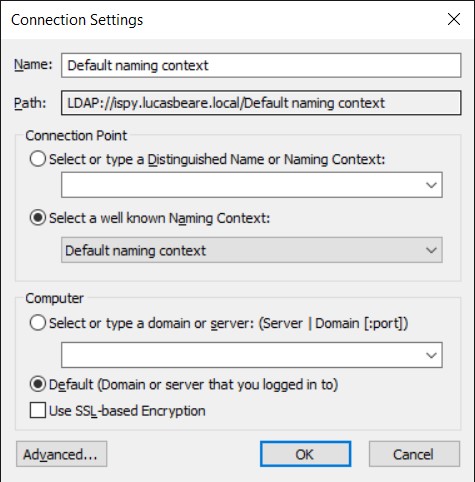
For Connection Point, click Select a well known Naming Context, and then click Configuration and then click ok.
Double-click Configuration, CN=Configuration,DC=ForestRootDomainName, CN=Services, and CN=Windows NT.
Right-click CN=Directory Service, and then click Properties.
In the Attribute column, click tombstoneLifetime.
Note the value in the Value column. If the value is not set, the value is 60 days.
How to log inefficient and expensive LDAP queries on a DC
Open regedit on the DC.
Go to: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ntds\Diagnostics
Change '15 Field Engineering' to a 5.
Inefficient and expensive LDAP queries will now show up in the Directory Services log under event ID 1644.
Common cause of account lockouts
Disconnected Terminal Server sessions can be a common cause of account lockouts. By default, disconnected sessions are maintained for an unlimited time on the server even though the user is no longer actively connected to the server. Running programs are kept active and a process that accesses network resources can do so with outdated authentication information. A disconnected session can have the same effect as a user with multiple interactive logons and causes an account lockout by using the outdated credentials.
More info
Sets a time limit for active but idle Terminal Services sessions - enabled - 1 hour
Set time limit for disconnected sessions - enabled - 1 day
Prevent a DC from authenticating/authorising users
A lower value that is entered for LdapSrvPriority indicates a higher priority. Clients will attempt to use a domain controller with an LdapSrvPriority setting of 0 before a domain controller with an LdapSrvPriority setting of 1, just as domain controllers with LdapSrvPriority settings of 1 would be used before domain controllers with LdapSrvPriority settings of 2.
Click Edit, click New, and then click DWORD value.
For the new value name, type LdapSrvPriority, and press ENTER.
Double-click the value name that you just typed to open the Edit DWORD Value dialog box.
Enter a value from 0 through 65535. The default value is 0.
Check secure channel between a member server and a domain controller
netdom verify /d:domain.com computername
Viewing objects and their attributes with repadmin
The showobjectmeta flag runs against a nominated DC and then checks for a nominated object (entered as a DN).
repadmin /showobjmeta enter_dc_name "CN=sampleuser,OU=AD,OU=AD2,OU=domain,DC=corp,DC=com,DC=au"
repadmin /showattr enter_DC_name CN=sampleuser,OU=AD,OU=AD2,OU=domain,DC=corp,DC=com,DC=au
Determine how many logon requests have been processed by a DC
nltest /server:dc_name /logon_query
Searching with ADSIEDIT
You can search for particular objects using ADSIEDIT. Open ADSIEDIT. Right click on ADSI Edit and select Connect to. In this example I will use the default naming context which is the domain partition. You can also connect to particular DCs, but by default it selects your authenticating DC. Note that you can also select other partitions like Schema and Configuration.
(&(objectCategory=user)(objectClass=user)(samAccountName=*beare*))
(&(objectCategory=group)(samAccountName=*groupname*))
Delegate permissions to add, delete and move computer objects in a particular OU
In ADUC right click on the desired OU and go to Properties - Security - Advanced - Add, then select principal (enter the group you are assigning permissions to), type – Allow.
Apply onto This object and all descendant objects
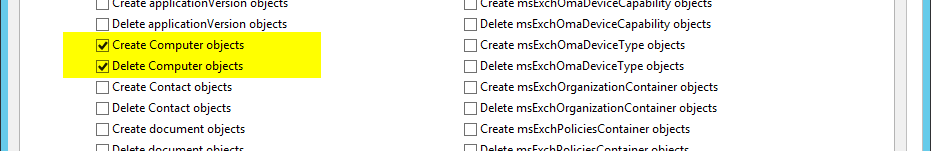
* Create Computer objects
* Delete Computer objects
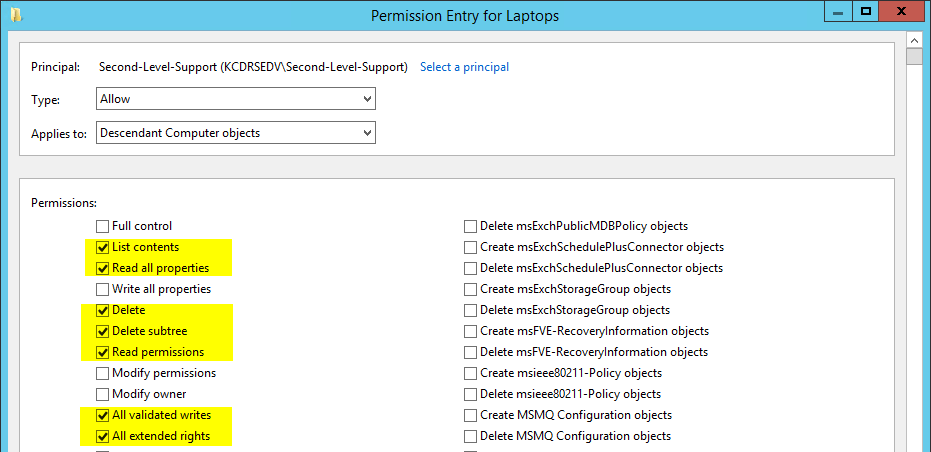
Apply onto Descendant Computer Objects
* List Contents
* Read All Properties
* Delete
* Delete Subtree
* Read Permissions
* All Validated Writes
* All Extended Rights
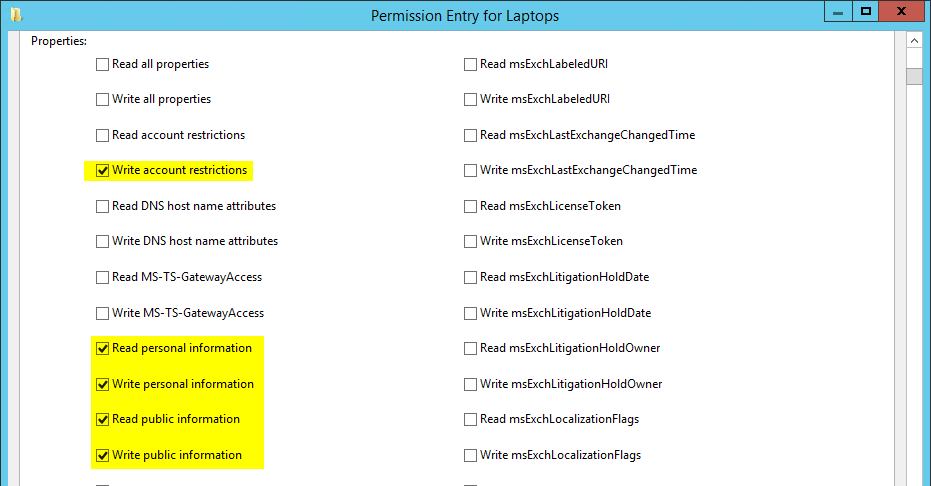
Apply onto Descendant Computer Objects
* Write Account Restrictions
* Write Computer name (pre-Windows 2000)
* Write Description
* Write msDS-User-Account-Control-Computed
* Write msDS-UserPasswordExpiryTimeComputed
* Write userParameters
* Read Personal Information
* Write Personal Information
* Read Public Information
* Write Public Information
Where do you point your Domain Controllers to for DNS?
DNS requests coming in hit the DNS server running on the DC, which then resolves and responds according to its own configuration which has nothing to do with the DNS server IP addresses configured on the network adapter properties. Those control the local DNS resolver, which operates completely independent of the DC DNS server, and comes into play only for requests generated locally, by software running on the DC itself.
What's the difference between the Reset password and Change password permissions on user objects in Active Directory (AD)?
The Change password permission requires that the person who changes the password know the account's current password. When an administrator or support person handles a user's forgotten password, the administrator or support person uses the Reset password permission, which doesn't require knowledge of the account's current password. With AD's default permissions, you can change your own password, but only Administrators and Account Operators can reset passwords.
How to Reset the DSRM Administrator Password on any version of Windows Server
This article describes how to reset the Directory Services Restore Mode (DSRM) administrator password for any server in your domain without restarting the server in DSRM. You cannot use the procedure that is described in this article if the target server is running in DSRM. A member of the Domain Administrators group sets the DSRM administrator password during the promotion process for the domain controller. You can use Ntdsutil.exe to reset this password for the server on which you are working, or for another domain controller in the domain.
At the Ntdsutil command prompt, type set dsrm password.
At the DSRM command prompt, type one of the following lines:
To reset the password on the server on which you are working, type reset password on server null. The null variable assumes that the DSRM password is being reset on the local computer. Type the new password when you are prompted. Note that no characters appear while you type the password.
To reset the password for another server, type reset password on server servername, where servername is the DNS name for the server on which you are resetting the DSRM password. Type the new password when you are prompted. Note that no characters appear while you type the password.
At the DSRM command prompt, type q.
At the Ntdsutil command prompt, type q to exit.
Source
Migrating from FRS to DFSR
Server 2003 uses FRS to replicate the contents of SYSVOL. When you've upgraded your domain to a 2008 DFL you can migrate to DFSR using dfsrmig. It's a four step process where DFSR runs alongside FRS and is eventually cutover. You can run dfsrmig /getmigrationstate to view the status of your migration to DFSR.
Migration guide
Backing up a 2003 DC's system state using NTBACKUP
The below script can be run using a scheduled task to create a date/time stamped .bkf file. From 2008 onwards you cannot using NTBACKUP and would need to use wbadmin. The log path for NTBACKUP is "C:\Documents and Settings\username\Local Settings\Application Data\Microsoft\Windows NT\NTBackup\data\".
for /f "Tokens=1" %%i in ('time /t') do set TM=-%%i
set TM=%TM::=-%
set DTT=%DT%%TM%
C:\WINDOWS\system32\ntbackup.exe backup systemstate /v:yes /r:no /rs:no /hc:off /j "System State Backup" /l:s /f "D:\Backups\%COMPUTERNAME%-system-state%DTT%.bkf"
Enabling cached logons
Allows users to log onto a domain joined computer even when a DC is unreachable.
GPO setting path:
Computer configuration - Windows Settings - Security Settings - Local Policies - Security Options - Interactive logon: Number of previous logons to cache (in case domain controller is not available).
A value of 0 disables logon caching. Any value above 50 only caches 50 logon attempts.
Setting how often a domain member should reset its computer account password
GPO settings path:
Computer configuration - Windows Settings - Security Settings - Local Policies - Security Options - Domain member: maximum machine account password age
How to properly apply a GPO to an individual user or computer
A common mistake here is to remove "Authenticated Users" directory from the Security Filtering section on the Group Policy Object.DONT DO THIS!!!
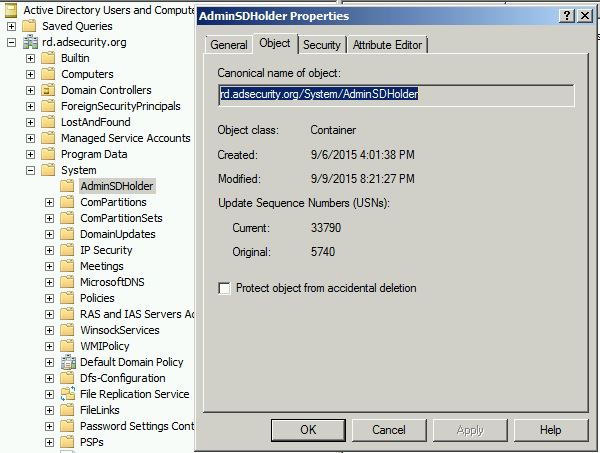
AdminSDHolder
An Active Directory domain has an object called AdminSDHolder, which resides in the System container of the domain (viewable in dsa.msc). The AdminSDHolder object has a unique Access Control List (ACL), which is used to control the permissions of security principals that are members of built-in privileged Active Directory groups eg Domain Admins (protected groups). Every hour, a background process runs on the domain controller that holds the PDC Emulator operations master role. It compares the ACL on all security principals (users, groups and computer accounts) that belong to protected groups against the ACL on the AdminSDHolder object. If a change in the protected object's ACL is detected it is overwritten to match the ACL on the AdminSDHolder object.
Source
What are LDAP Binds?
Binding is the step where the LDAP server authenticates the client and, if the client is successfully authenticated, allows the client access to the LDAP server based on that client's privileges.
How To Enable DNS Auditing
Firstly Enable Directory Service Access auditing on your DC via group policy:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Audit Policy
Define ‘Audit directory service access’ for success and failure.
Source
Backing up the systemstate (AD) with wbadmin
Add the Windows Server backup feature:
Add-WindowsFeature windows-server-backup -includeallsubfeature
wbadmin start systemstatebackup -backupTarget:
(i.e. wbadmin start systemstatebackup -backupTarget:f:)
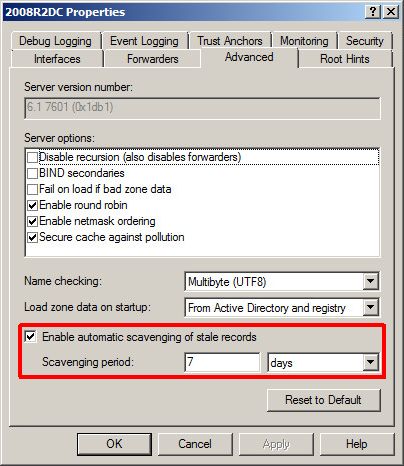
Show which DCs have DNS Scavenging enabled
A DC that reports a value other than 0 has DNS scavenging enabled. Note, a DNS zone held by the DC would also need to have scavenging enabled for it to take effect.
foreach ($dc in $dcs)
{
$output = dnscmd $dc /info
$string = $output | select-string "Scavenging"
write-host $dc
write-host $string
write-host ""
}
Understanding DNS Scavenging
On the DNS zone where scavenging is set there are two intervals set.
Convert 18-digit LDAP/FILETIME timestamps to human readable date
The 18-digit Active Directory timestamps, also named 'Windows NT time format' and 'Win32 FILETIME or SYSTEMTIME'. These are used in Microsoft Active Directory for pwdLastSet, accountExpires, LastLogon, LastLogonTimestamp and LastPwdSet. The timestamp is the number of 100-nanoseconds intervals (1 nanosecond = one billionth of a second) since Jan 1, 1601 UTC.
w32tm.exe /ntte 131001091660000000
Demote a 2012 Domain Controller using powershell
Running the below cmdlet without additional options will demote a DC and make the server a member server. The AD tools and DNS role will remain. As long as this DC is not the last DC in the domain, the domain will not be removed.
Uninstall-ADDSDomainController
Link
Seizing FSMO roles
When a domain controller that holds FSMO roles crashes or is removed from network, you won't be able to gracefully transfer the roles to another server, you will need to sieze them. Once the roles are seized, the server should never return to the network, unless it is rebuilt. After seizing the roles make sure you perform a Metadata cleanup of the crashed DC.
ntdsutil (enter)
ntdsutil: roles (enter)
fsmo maintenance: connections (enter)
server connections: connect to server
server connections: quit (enter)
fsmo maintenance: seize schema master (enter)
2003 server:fsmo maintenance: seize domain naming master (enter)
2008 server: fsmo maintenance: seize naming master (enter)
fsmo maintenance: seize rid master (enter)
fsmo maintenance: seize pdc (enter)
fsmo maintenance: seize infrastructure master (enter)
fsmo maintenance: quit (enter)
ntdsutil: quit (enter)
What is the _msdcs DNS zone?
Link